Objectives ⬇
- Describe the essential components of computer systems, including hardware and software.
- Recognize the rapid evolution of computer systems and the benefit of keeping up to date with current trends and developments.
- Analyze how computer systems function as tools for managing information and generating knowledge.
- Define the concept of human-technology interfaces.
- Assess how computers can support collaboration, networking, and information exchange.
Key Terms ⬆ ⬇
Introduction ⬆ ⬇
In this chapter, the discipline of computer science, which is one of the building blocks of nursing informatics, is introduced through a focus on computers and the hardware and software that comprise these evolving systems (Figure 3-1). Computer science offers extremely valuable tools that, when used skillfully, can facilitate the acquisition and manipulation of data and information by nurses who then can synthesize the data into an evolving knowledge and wisdom base. This process can facilitate professional development and the ability to apply evidence-based practice decisions within nursing care, and if the results are disseminated and shared, they can also advance the professional knowledge base.
Figure 3-1 Building Blocks of Nursing Informatics
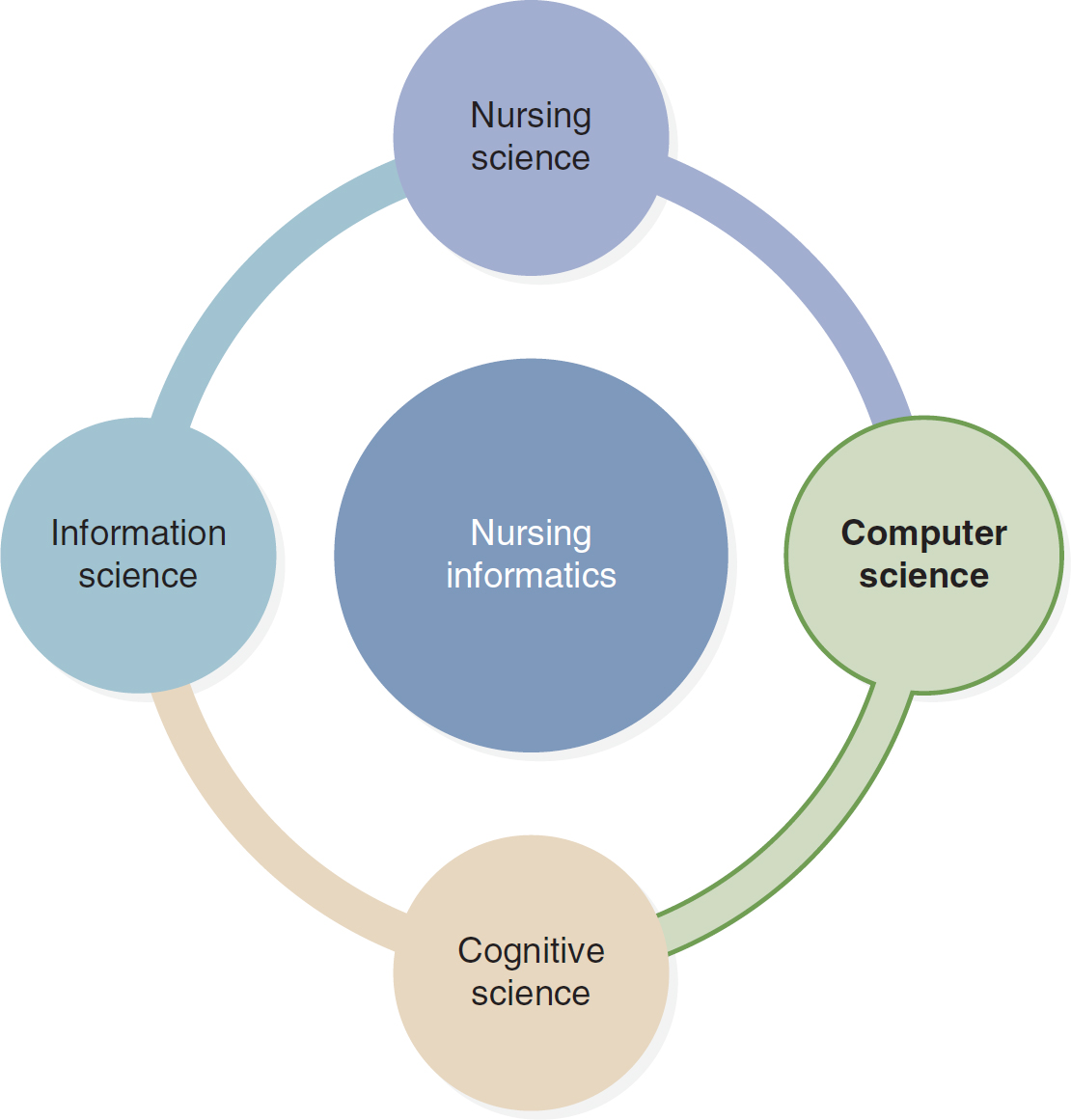
The four building blocks of nursing informatics include nursing science, computer science, cognitive science, and information science.
This chapter begins with a look at common computer hardware, followed by a brief overview of operating, productivity, creativity, and communication software. It concludes with a glimpse at how computer systems help to shape knowledge and collaboration and an introduction to human-technology interface dynamics.
The Computer as a Tool for Managing Information and Generating Knowledge ⬆ ⬇
Throughout history, various milestones have signaled discoveries, inventions, and philosophical shifts that spurred a surge in knowledge and understanding within the human race. The advent of the computer is one such milestone, which has sparked an intellectual metamorphosis whose boundaries have yet to be fully understood. Computer technology has ushered in what has been called the Information Age, an age when data, information, and knowledge are both accessible and manipulable by more people than ever before. How can a mere machine lead to such a revolutionary state of knowledge potential? To begin to answer this question, we need to examine the basic structure and components of computer systems.
Essentially, a computer is an electronic information-processing machine that serves as a tool with which to manipulate data and information. The easiest way to begin to understand computers is to realize that they are input-output systems. These unique machines accept data input via a variety of devices, process data through logical and arithmetic rendering, store the data in memory components, and output data and information to the user.
“Computing has changed the world more than any other invention of the past hundred years, and has come to pervade nearly all human endeavors. Yet, we are just at the beginning of the computing revolution; today's computing offers just a glimpse of the potential impact of computers” (Evans, 2019, p. 3). Computer manufacturers and researchers, such as Intel, have identified the need to design computers to mask this growing complexity and sophistication by enhancing ease of use or user-friendly aspects. This is being achieved by honing hardware and software capabilities until they work together seamlessly to ensure user-friendly, intuitive tools for users of all levels of expertise. An example is in the haptic technologies, evolving hardware and software that will increase the experiential aspects of computing. Box 3-1 provides information about haptic technology.
| Box 3-1 Haptic Technology |
|---|
| Dee McGonigle
The science of haptics deals with artificial touch technology. Haptics is touted as the evolving technology needed to advance virtual reality (VR) and augmented reality (AR) beyond just seeing and hearing within a virtual world in VR or the floating interfaces of AR to actually feel what you are touching or what comes in contact with you if you have a body suit. On its website, Immersion states that “real, immersive, and more appealing: haptics adds value to the experience” (www.immersion.com), thus enhancing digital experiences. No matter what reality we are experiencing, our emotions and experiences are heightened, or come alive, through our sense of touch, and it is haptic technology that allows the user to reproduce that sensation. The user can feel the technology, or experience, through a series of actions, including force and vibration or carefully controlled haptic virtual objects, and as the technology improves, so will the virtual feeling that improves the immersive experience. Effective learning environments will provide an excellent integration of visual and audible perceptions with tactile sensations.
Haptic technology is being built into partial- and full-body suits. According to VR Electronics, its wearable “TESLASUIT training solution provides outputs from haptic feedback and climate control to users and receives inputs from motion capture and biometrics. With our software and partner ecosystem, this technology is a complete solution for improving human performance” (https://teslasuit.io). This suit can be used by rehabilitation professionals to facilitate the user's learning or relearning physical actions and training their reflexes.
Haptic gloves as well continue to evolve.
VR Life reviewed the top haptic gloves for VR in 2022 (Bithrey, 2022). VR Life thinks the best gloves are the SensoryX VR Free Gloves, which can work with all VR HMDs. The SensoryX website (https://sensoryx.tech) states that they are the tracking solution for the metaverse and the user interaction of the future.
LEAPMotion, a company that designs motion control devices, wants to “build a more human reality.” The Ultraleap Gemini is the fifth-generation hand-tracking platform, which has improved tracking for both hands, especially when they are close together, interacting, or actually overlapping (https://developer.leapmotion.com/about-gemini). The Make Use Of website describes the Oculus Quest as being capable of using the headset's external cameras to track your finger motion and hand movement to use as input (Stegner, 2022).
Reflect on the ramifications of the computer and digital enhancements for health care and education, especially as they relate to the haptic experience and wearables.
|
The goal for vendors that provide computer systems and software is to decrease the learning curve for users while enhancing their capacity to manipulate the system to meet their computing needs. Therefore, the complexity of the operation is concealed by its ease of use.
Computers are universal machines because they are general-purpose, symbol-manipulating devices that can perform any task represented in specific programs. For instance, they can be used to draw an image, calculate statistics, write an essay, or record nursing care data. In a nutshell, computers can be used for data and information storage, retrieval, analysis, generation, and transformation.
Most computers are based on scientist John von Neumann's model of a processor-memory-input-output architecture. This basic configuration and the components are briefly reviewed (see Table 3-1 and Figure 3-2).
Figure 3-2 Computer Components
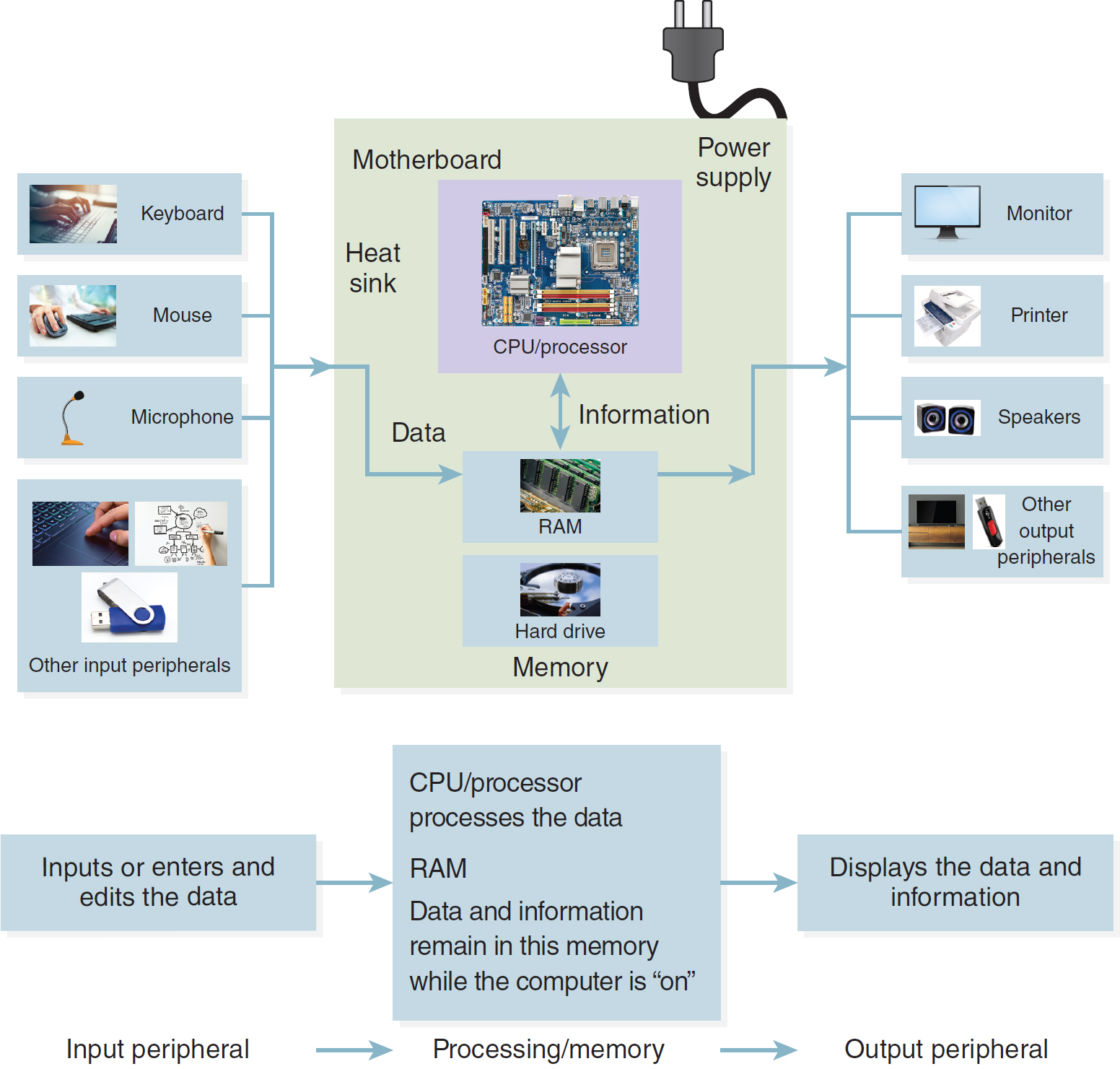
A flow diagram illustrates the interconnected components of a computer system.
The primary components are arranged around a central motherboard, each illustrated with accompanying photos. 1. Motherboard: Comprising the power supply, heat sink, C P U or processor, RAM, and memory with a hard drive. 2. Input peripherals: Encompassing the keyboard, mouse, microphone, and other input devices like U S B drives and touch pens. 3. Output peripherals: Including the monitor, printer, speakers, and other output devices such as projectors. The sequential flow of data through the computer components follows this process. Input peripheral: Inputs or enters and edits data. Processing and memory: The C P U or processor processes the data, and the RAM retains data and information while the computer is on. Output peripheral: Displays the processed data and information.
Keyboard © Undrey/Shutterstock; mouse © Pressmaster/Shutterstock; microphone © VectorShow/Shutterstock; touch pad © donfiore/Shutterstock; pen drawing a diagram © Syda Productions/Shutterstock; USB drive © DecemberDah/Shutterstock; CPU © Peter Gudella/Dreamstime.com; RAM © NorGal/Shutterstock; hard drive © mike mols/Shutterstock; monitor © Leone_V/Shutterstock; printer © Billion Photos/Shutterstock; speakers © Krailurk Warasup/Shutterstock; TV © JTal/Shutterstock; flash drive © Ksander/Shutterstock
Table 3-1 ComponentsComponent | Description |
|---|
Hardware | Actual physical body of the computer and its components. |
Central processing unit (CPU) | CPU is an older term for the processor and microprocessor. Sometimes conceptualized as the brain, or command center, directing the actions of all computer components; executes, calculates, and processes the binary computer code (which consists of various configurations of 0s and 1s), which are functions that are instigated by the operating system (OS) and other applications on the computer. Manages both incoming and outgoing data that are processed across components. The processor contains specific mechanical units, including registers, arithmetic logic units; a floating point unit; control circuitry; and cache memory. Cache memory is extremely quick memory that holds whatever data and code are being used at any one time. The speed and power of a processor are measured in gigahertz (1 GHz). Multicore microprocessors, or chips that combine two or more processors, have become a standard in both personal and professional computers. For more information, refer to UL Benchmarks (2023). |
Motherboard | Known as the central nervous system of the computer, it facilitates communication among all the computer components since the components are connected to it in some way (either directly via local sockets, attached directly to it, or connected via cables). These components include universal serial bus (USB), Ethernet network, and integrated graphics controllers. |
Power supply | A critical component because it provides the essential electrical energy needed to allow a computer to operate. |
Hard disk, or hard drive | The rigid hard disks acting as permanent data storage holding gigabytes (GB) or terabytes (TB) of data, information, documents, and programs saved on the computer, even when the computer is turned off. These disk drives are not infallible, however, so backing up important data is imperative. |
Random-access memory (RAM) | RAM is considered to be volatile memory because it is a temporary storage system that allows the processor to access program codes and data while working on a task. The contents of RAM are lost once the system is rebooted or shut off intentionally or because of a loss of power. Computers can gain more RAM via graphics cards and other expansion cards. A certain portion of the RAM, called the main memory, serves the hard disk and facilitates interactions between the hard disk and the CPU. Main memory is provided by dynamic random-access memory (DRAM) and synchronous dynamic random-access memory (SDRAM). Newer chips, double data rate synchronous dynamic random-access memory (DDR SDRAM), allow for greater bandwidth and twice the transfers per the unit of time of the computer's internal clock. |
Read-only memory (ROM) | ROM stores saved data and is critical in the working of the computer's OS and other activities. ROM is stored primarily on the motherboard, but it may also be available through the graphics card, other expansion cards, and peripherals. In recent years, rewritable ROM chips, which may include other forms of ROM, such as programmable read-only memory (PROM), erasable ROM, electronically erasable programmable read-only memory (EEPROM), and flash memory (a variation of EEPROM), have become available. |
Basic input/output system (BIOS) | BIOS is a specific type of ROM used by the computer when it first boots up to establish basic communication among the processor, motherboard, and other components. It controls the computer from the time the machine is switched on until the primary OS takes over. The firmware initializes the hardware and boots (loads and executes) the primary OS. |
Virtual memory | A special type of memory that is stored on the hard disk to provide temporary data storage so that data can be swapped in and out of the RAM as needed. |
Peripheral component interconnection (PCI) bus | This component is important for connecting additional plug-in components to the computer. It uses a series of slots on the motherboard to allow peripheral component interconnection (PCI) card plug-ins. |
Small computer system interface (SCSI) | The SCSI component provides the means to attach additional devices, such as scanners and extra hard drives. |
DVD/CD drives | The compact disk read-only memory (CD-ROM) drive reads and records data to portable CDs. The light reflected on the disk is directed by a system of lenses to a photodetector, which converts the light pulses into an electrical signal; this signal is then decoded by the drive electronics to the motherboard. There are compact disk-recordable (CD-R), compact disk-rewritable (CD-RW), digital video disk-recordable (DVD-R), and digital video disk-rewritable (DVD-RW) drives. |
Flash or USB flash drive | This portable memory device uses electronically erasable, programmable ROM to provide fast, permanent memory. The USB flash drive is typically a removable and rewritable device that includes flash memory and an integrated USB interface. |
Modem | Can be situated either externally or internally; enables internet connectivity via a cable connection through network adapters situated within the computer apparatus. |
Connection ports | These ports allow data to move to and from the computer via peripheral or storage devices and are made to fit different types of plug-in devices, including monitor cable, keyboard, mouse, network cable, microphone/speaker/auxiliary input, USB, and printer ports (SCSI or parallel). |
Cards | Graphics card: Most computers have a graphics accelerator card slotted in the microprocessor to process image data and output those data to the monitor. If a user intends to create or view three-dimensional images or is an active game user, an enhanced graphics card generally must be installed. Video adapter cards: Provide video memory, a video processor, and a digital-to-analog converter that works with the processor to output high-quality video images to the monitor. Sound card: Converts digital data into an analog signal, which is then outputted to the computer's speakers or headphones. The reverse is also accomplished by inputting a signal from a microphone or other audio-recording equipment, which then converts the analog signal to a digital signal. |
Binary System and Storage Bit
A bit is the smallest possible chunk of data memory used in computer processing and is depicted as either a 1 or a 0. Bits make up the binary system of the computer.
Byte
A byte is a chunk of memory that consists of 8 bits and is the best way to indicate computer memory or storage capacity. In modern computers, bytes are described in units of megabytes (MB), gigabytes (GB) (1 GB equals 1,000 MB), or terabytes (TB) (1 TB equals 1 trillion bytes, or 1,000 GB). Box 3-2 discusses the various storage capacities.
| Box 3-2 Storage Capacities |
|---|
| Dee McGonigle KathleenMastrian
Storage and memory capacities are evolving. In the past few decades, great leaps in data storage have been made. All storage capacity begins with the bit. The files on a computer are stored as binary files. The software that is used translates these binary files into words, numbers, pictures, images, or video. Using this binary code in the binary numbering system, measurement is counted by factors of 2, such as 1, 2, 4, 8, 16, 32, 64, and 128. These multiples of the binary system in computer usage are also prefixed based on the metric system. Therefore, a kilobyte (KB) is actually 2 to the 10th power (or 210), or 1,024 bytes, but it is typically considered to be 1,000 bytes. That is why you will see 1,024 or multiples of that number, instead of an even 1,000, mentioned at times in relation to kilobytes.
As capabilities soared, so did the ability to save and store what was used and created, and so the megabyte (MB) emerged as a common unit of measure (1 MB is 1,048,576 bytes but roughly equivalent to 1 million bytes). The next leap in computer capacity is a gigabyte (GB) (1 GB is 1,073,741,824 bytes but is generally rounded to 1 billion bytes). Some computing experts are very concerned that valuable bytes are lost when these measurements are rounded, whereas hard-drive manufacturers use the decimal system so that capacity is expressed as an even 1 billion bytes per gigabyte.
Computer capacity has moved into and beyond the range of terabytes, with capacities moving into the range of petabytes (PB), exabytes (EB), zettabytes (ZB), and yottabytes (YB). These terms for storage capacity are defined as follows:
|
- 1 TB = 1,000 GB
- 1 PB = 1,000,000 GB
- 1 EB = 1,000 PB
- 1 ZB = 1,000 EB
- 1 YB = 1,000 ZB
To put all of this in perspective, Lyman and Varian (2003) described the data powers of 10 as follows: - 2 KB: A typewritten page
- 2 MB: A high-resolution photograph
- 10 MB: A minute of high-fidelity sound or a digital chest X-ray
- 50 MB: A digital mammogram
- 1 GB: A symphony in high-fidelity sound or a movie at TV quality
- 1 TB: All the X-ray films in a large, technologically advanced hospital
- 2 PB: The contents of all U.S. academic research libraries
- 5 EB: All words ever spoken by human beings
And we have not even addressed zettabytes (ZB) and yottabytes (YB), so stay tuned. |
Software
Software comprises the application programs developed to facilitate various user functions, such as writing, artwork, organizing meetings, surfing the internet, and communicating with others. For the purposes of this overview, the various types of software have been divided into four categories: (1) OS software, (2) productivity software, (3) creativity software, and (4) communication software.
User friendliness is a critical condition for effective software adoption. How user friendly the software is to users is based on their perception of how clear the package is to understand and to use. The rapid evolution of hardware mentioned previously has been equally matched by the phenomenal development in software over the past three or four decades (see Table 3-2 for a brief review of software).
Table 3-2 SoftwareSoftware | Description |
|---|
Commercial | Several large commercial software companies, such as Apple, Microsoft, IBM, and Adobe, dominate the market and have done so since the advent of the personal computer (PC). Licensed software has evolved over time; hence, most products have a long version history. Many software packages, such as office suites, are expensive to purchase; in turn, there is a digital divide as far as access and affordability go across societal spheres, especially when viewed from a global perspective. |
Open source | The open source initiative began in the late 1990s and has become a powerful movement that is changing the software production and consumer market. In addition to commercially available software, a growing number of open source software packages are being developed in all four of the categories addressed in this chapter. The open source movement was begun by developers who wished to offer their creations to others for the good of the community and encouraged them to do the same. Users who modify or contribute to the evolution of open source software are obligated to share their new code, but essentially the software is free to all. Apache OpenOffice, Google Docs, and NeoOffice are examples of open source productivity software (Figure 3-3). |
Operating system (OS) | The OS is the most important software on any computer. It is the very first program to load upon start-up and is fundamental for the operation of all other software and the computer hardware since it provides a reliable, consistent interface for the software applications to work with the computer's hardware. Examples of commonly used OSs include the Microsoft Windows family, Linux, and Mac OS. An OS must be both powerful and flexible to adapt to the myriad types of software available, which are made by a variety of development companies. New versions of the major OSs are equipped to deal with multiple users and handle multitasking with ease. For example, a user can work on a word processing document while listening for an email-received signal, have an internet browser window open to look for references on the internet as needed, listen to music in the background, and download a file-all at the same time. OS tasks can be described in terms of six basic processes: A GUI (pronounced “gooey”) is used by OSs to display a combination of graphics and text, such as icons, drop-down menus, and buttons; it allows one to use input and output devices as well as icons that represent files, programs, actions, and processes. OSs should be convenient to use, easy to learn, reliable, safe, secure, and fast. They should also be easy to design, implement, and maintain while being flexible, compatible, portable, reliable, error-free, extensible, and efficient. |
Productivity | Productivity software, such as an office suite, is the type of software most commonly used in the workplace and on personal computers. It typically bundles together word processing, spreadsheet, database, presentation, web development, and email programs. The intent of office suites is to provide all the basic programs that office or knowledge workers need to do their work. The bundled programs within the suite are organized to be compatible with one another and designed to look similar to one another for ease of use and provide a powerful array of tools for data manipulation, information gathering, and knowledge generation. Some office suites add other programs, such as database creation software, mathematical editors, and drawing and desktop publishing programs. Table 3-3 summarizes the application of programs included in some of the popular office suites: Microsoft Office, Apache OpenOffice, and WordPerfect Suite. |
Creativity | Creativity software includes programs that allow users to draw, paint, render, record music and sound, and incorporate digital video and other multimedia in professional aesthetic ways to share and convey information and knowledge (Table 3-4). |
Communication | Networking and communication software enable users to dialogue, share, and network with other users via email or instant message (IM), by accessing the World Wide Web (WWW), or by engaging in virtual meetings using conferencing software (Table 3-5). |
Figure 3-3 Open Source Software
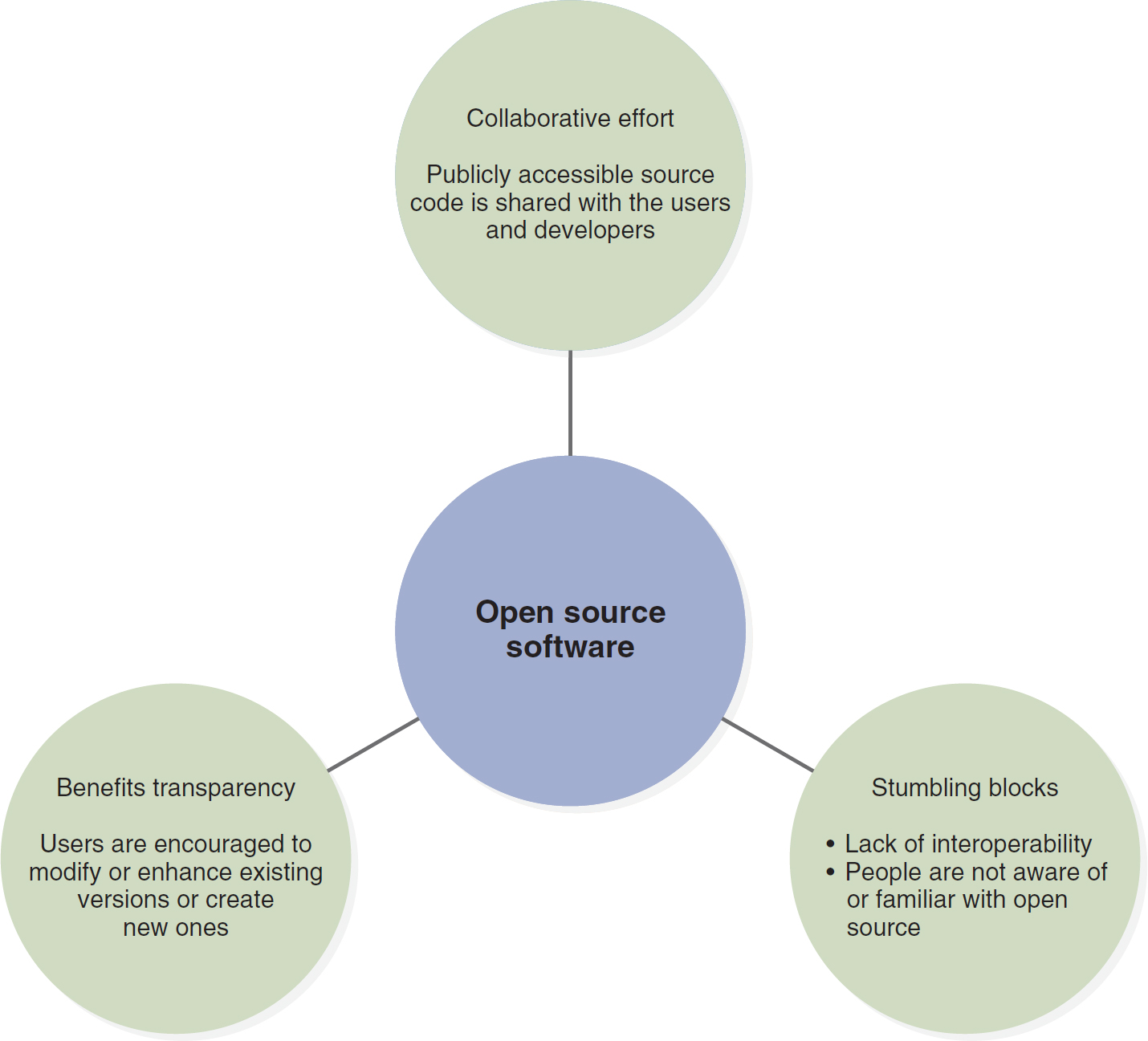
An illustration depicts the benefits and challenges of open source software.
Benefits include transparency, as users are encouraged to modify or enhance existing versions or create new ones through collaborative efforts. The collaborative efforts emphasize that publicly accessible source code is shared with users and developers. Stumbling blocks include a lack of interoperability and limited awareness or familiarity of people with open source concepts.
Table 3-3 Productivity: Office Suite Software Features and ExamplesProgram | Application | Examples |
|---|
Word processing | Composition, editing, formatting, and producing text documents | Microsoft Word, OpenOffice Writer, KOffice KWord, Corel WordPerfect or Corel Write, Apple Pages, and Apache OpenOffice |
Spreadsheets | Grid-based documents in ledger format; organize numbers and text and calculate statistical formulae | Microsoft Excel, OpenOffice Calc, KOffice KSpread, Corel Quattro Pro, Apple Numbers, and Apache OpenOffice |
Presentations | Slideshow software, usually used for business or classroom presentations, using text, images, graphs, and media | Microsoft PowerPoint, OpenOffice Impress, KOffice KPresenter, Corel Show, Apple Keynote, and Apache OpenOffice |
Databases | Database creation for text and numbers | Microsoft Access (in elite packages), OpenOffice Base, KOffice Kexi, Corel Calculate, Corel Paradox |
Email | Integrated email program to send and receive electronic mail | Microsoft Outlook, Corel WordPerfect Mail, Mozilla Thunderbird |
Drawing | Graphics and diagram drawing | OpenOffice Draw, Corel Presentation Graphics, KOffice Kivio, Karbon, Krita |
Math formulas | Insert math equations in word processing and presentation work | OpenOffice Math, KOffice KFormula |
Desktop publishing | Page layouts and publication-ready documents | Microsoft Publisher (in elite packages), Apple Pages |
Table 3-4 Creative Software Features and ExamplesProgram and Application | Software Examples |
|---|
Raster graphics programs |
Draw, paint, render, manipulate, and edit images, fonts, and photographs to create pixel-based (dot points) digital art and graphics. | Adobe Photoshop and Fireworks; Ulead PhotoImpact; CorelDRAW, Painter, and PaintShop Pro; GIMP (open source); KOffice; Krita (open source) |
Vector graphics programs |
Mathematically rendered geometric modeling is applied through shapes, curves, lines, and points and manipulated for shape, color, and size. Ideal for printing and three-dimensional (3D) modeling. | Adobe Flash, FreeHand, and Illustrator; CorelDRAW and Designer; OpenOffice Draw (open source); Microsoft Visio; Xara Xtreme; KOffice Karbon14 (open source) |
Desktop publishing programs |
Page layout and publishing preparation for printed and web documents, such as magazines, journals, books, newsletters, and brochures. | Adobe InDesign, Corel PageMaker, Microsoft Publisher, Scribus (open source), QuarkXPress, Apple Pages (note that many of the graphics programs can also be used for desktop publishing) |
Web design programs |
Create, edit, and update webpages using specific codes, such as XML, CSS, HTML, and Java. | Adobe Dreamweaver, Word Press, Microsoft FrontPage, Nvu (open source), W3C's Amaya (open source) |
Multimedia programs |
Combine text, audio, images, animation, and video into interactive content for electronic presentation. | Adobe Flash, Microsoft Movie Maker, Apple QuickTime and FinalCut Studio, Corel VideoStudio, Ulead VideoStudio, Real Studio, CamStudio (open source), Audacity (open source) |
Table 3-5 Communication Software Features and ExamplesProgram and Application | Software Examples |
|---|
Email client |
Allows user to read, edit, forward, and send email messages to other users via an internet connection. The software can be resident on the computer or accessed via the World Wide Web. | Resident programs Microsoft Outlook and Outlook Express, Eudora, Pegasus, Mozilla Thunderbird, Lotus Notes Web-based programs Gmail, Yahoo Mail, Hotmail |
Internet browsers |
Enables user to access, browse, download, upload, and interact with text, audio, video, and other web-based documents. | Mozilla Firefox, Microsoft Internet Explorer and Edge, Google Chrome, Apple Safari, Opera, microbrowsers (for mobile access) |
Instant messaging (IM) |
Real-time text messaging between users; can attach images, videos, and other documents via personal computer, cell phone, and handheld devices. | MSN Instant Messenger, Microsoft Live Messenger, Yahoo Messenger, Apple iChat |
Conferencing |
Enables user to communicate in a virtual meeting room setting to share work, discussions, or planning using an intranet or internet environment; can exhibit files, video, and screenshots of content. | Adobe Acrobat Connect, Microsoft Live Meeting or Meeting Space, Microsoft Teams, GoToMeeting, Meeting Bridge, Free Conference, RainDance, WebEx, Zoom |
Acquisition of Data and Information: Input Components
Input devices include keyboard; mouse; joystick (typically used for playing computer games); game controller or pad; web camera (webcam); stylus (often used with tablets or personal digital assistants); image scanner for copying a digital image of a document or picture; touch pad; or other plug-and-play input devices, such as a digital camera, digital video recorder (camcorder), MPEG-1 Audio Layer-3 (MP3) player, electronic musical instrument, and physiological monitor. These devices are the media used to input text or visual, audio, or multimedia data into the computer system for viewing, listening, manipulating, creating, or editing. The primary input devices on a computer are the keyboard, mouse, touch pad, and touch screen. See Table 3-6 for a brief overview of the typical input devices.
Table 3-6 Typical Input DevicesInput Component | Description |
|---|
Keyboard | A computer keyboard is very similar to the typewriter keyboards of earlier days and usually serves as the primary input device that enables the user to type words, numbers, and commands into the computer's programs. Typically, standard computer keyboards are organized to facilitate Latin-based languages using a QWERTY layout (so named because these letters appear on the first six keys in the first row of letters). Certain keys are used as command keys, particularly the control (CTRL), alternate (Alt), delete (Del), and shift keys, all of which can be used to activate useful commands. The escape (ESC) key allows the user to instantly exit a process or program. Some keyboards have a wire and a plug-in, whereas others are wireless, or cordless. Touch screen, or virtual, keyboards are incorporated into the touch screens of phones, gaming machines, and tablets, and they are also available through ease-of-access tools on laptops. |
Mouse | The mouse is the second most commonly used input device. It is manipulated by the user's hand to point, click, and move objects around on the computer screen. A mouse can come in a number of configurations, including a standard mechanical trackball serial mouse, bus mouse, PS/2 mouse, USB-connected mouse, optical lens mouse, cordless mouse, and optomechanical mouse. It has evolved and increased in complexity and capability over time. Most gaming mice have become sophisticated with customizable features, such as programmable macro commands and on-the-fly resolution switching. |
Touch pad | A device that senses the pressure of the user's finger along with the movement of the finger on the touch pad to control input positioning. It is an alternative to using a mouse. |
Touch screen | The touch screen is a display used as an input device for interacting with or relating to the display's materials or content. The user can touch or press on the designated display area to respond to, execute, or request information or output. |
Processing of Data and Information: Throughput/Processing Components
All the hardware discussed earlier in this chapter is involved in the throughput, or processing, of input data and the preparation of output data and information. Specific software is used, depending on the application and data involved. One key hardware component, the computer monitor, is a unique example of a visible throughput component; it is the part of the computer that users focus on the most when they are working on a computer. Input data can be visualized and accessed by manipulating the mouse and keyboard input devices, but the monitor is what the user focuses on. The monitor is critical for the efficient rendering or image synthesis so that the data, information, and images can be visualized during this part of the cycle because it facilitates user access and control of the data and information.
Monitor
The monitor is the visual display that serves as the landscape for all interactions between the user and the machine. Some computer monitors also have a touch screen, which can serve as an input device when the user touches specific areas of the screen. Monitors vary in their refresh rate and dot pitch, and both are important for user comfort. The faster the refresh rate, the cleaner and clearer the image on the screen because the monitor refreshes the screen contents more frequently. Similarly, the larger the dot pitch factor, the smaller the dots that make up the screen image, which provides a more detailed display on the monitor and facilitates clarity and ease of viewing.
If equipped with a touch screen, a monitor can also serve as an input device when activated by a stylus or finger pressure. Some users might also consider the monitor to be an output device because access to input and stored documents is often performed via the screen (e.g., reading a document that is stored on the computer or viewable from the internet). As we advance to more engaged computing, larger screens and ultrawide monitors are evolving to provide immersive experiences.
Smartphone displays can be a form of active-matrix organic light-emitting diode (AMOLED) or in-plane switching liquid-crystal display (IPS LCD). In the AMOLED type of display, the individual pixels are lit separately (active matrix); the next-generation super AMOLED type of display includes touch sensors.
Dissemination: Output Components
Output devices carry data in a usable form through exit devices in or attached to a computer. Common forms of output include printed documents; audio or video files; physiological summaries; scan results; and saved files on portable disk drives, a flash drive, or an external hard drive. Output devices literally put data and information at the user's fingertips, which can then be used to develop knowledge and even wisdom. The most commonly used output devices include printers, speakers, and portable disk drives.
Printer
Printers are external components that can be attached to a computer enabling users to print a hard copy of documents that are housed on the computer.
Printers are typically all-in-one machines, meaning they can print, scan, fax, and copy. There are printers that can be accessed via the internet using Wi-Fi. There are also three-dimensional (3D) printers that can create a 3D solid object produced layer by layer from a 3D software digital file.
Speakers
All computers have some sort of speaker setup, usually small speakers embedded in the monitor or in the case, or if it is a laptop, close to the keyboard. Often, external speakers are added to a computer system to provide enhanced sound and a more enjoyable listening experience.
What Is the Relationship of Computer Science to Knowledge? ⬆ ⬇
Scholars and researchers understand the effects that computer systems, architecture, applications, and processes have on the potential for knowledge acquisition and development. Users who have access to contemporary computers equipped with full internet access have extensive resources at their fingertips such as entire library collections. Users are also able to contribute to the development of knowledge through the use of productivity, creativity, and communication software and are able to disseminate knowledge on a grand scale with other users. This deluge of information available via computers must be mastered and organized by the user if knowledge is to emerge. Discernment and the ability to critique and filter this information must also be present to facilitate the further development of wisdom.
The development of an understanding of computer science principles as they apply to technology used in nursing can facilitate optimal usage of the technology for knowledge development and dissemination in the profession. The maxim that knowledge is power and that the skillful use of computers lies at the heart of this power is a presumption. Once nurses become comfortable with the various technologies, they can shape, refine, and apply them in new and different ways, just as they have always adapted equipment and technologies. Nurses must harness the power of data and information through the use of computer technologies to build knowledge and gain wisdom.
How Does the Computer Support Collaboration and Information Exchange? ⬆ ⬇
Computers can be linked to other computers through networking software and hardware to promote communication, information exchange, work sharing, and collaboration. Networks can be
- local or organizationally based, with computers joined together into a local area network (LAN);
- organized on a wider area scope such as a city or distinct geographic area, such as a cable TV network, using a metropolitan area network (MAN) typically comprising several LANs that are interconnected over a dedicated backbone connection; and
- encompassing computers at an even greater distance, such as a country, continent, or even the internet itself, using a wide area network (WAN).
Network interface cards are used to connect a computer and its modem to a network. A virtual private network (VPN) provides secure and private connectivity between networks and remote computers or devices using encryption, which transforms information or data into a code to prevent unauthorized access.
Networks within health care can manifest in several configurations, including client-focused networks, such as in telenursing, e-health, and client support networks; work-related networks, including virtual work and virtual social networks; and learning and research networks, as in communities of practice. These trends are still evolving in most nursing work environments (and most nurses' personal lives), but they are growing dramatically. We are experiencing one of the greatest upsurges in shared information and our ability to access, exchange, and utilize this information to enhance knowledge.
Virtual social networks are another form of professional network that have expanded phenomenally since the advent of the internet and other computer software and hardware. Nursing-related virtual social networks provide a cyberspace for nurses to make contacts, share information and ideas, and build a sense of community.
Social communication software is used to provide a dynamic virtual environment, and often virtual social networks provide communicative capabilities through posting tools, such as blogs, forums, and wikis; email for sharing ideas on a smaller scale; collaborative areas for interaction and creating and building digital artifacts or planning projects; navigation tools for moving through the virtual network landscape; and profiles to provide a space for each member to disclose personal information with others. Nurses engaged in shift work often find that virtual social networks can provide a sense of connection with other professionals that is available around the clock. Because time is often a factor in any social interchange, virtual communication offers an alternative for practicing nurses. With active participation, the interchanges and shared information and ideas of the network can culminate in valuable social and cultural capital, which is available to all members of that network. Often, nursing virtual social networks are created for the purpose of exchanging ideas on practice issues and best practices; becoming more knowledgeable about new trends, research, and innovations in health care; or participating in advocacy, activist, and educational initiatives.
Through the use of portable disk devices, such as flash drives, as well as web-based and cloud spaces, people can share information, documents, and communications by exchanging files. The World Wide Web has evolved to become a viable and user-friendly way for people to collaborate and exchange information; projects; and other knowledge-based files, such as websites, email, social networking applications, and webinar logs.
Mobile Computing ⬆ ⬇
Mobile computing is a technology that allows human-computer interaction wherever you are by transporting the capability of transmitting data, voice, and video with you, whether you are moving or standing still. A mobile OS is different from a computer's OS in one important way, being designed for mobile use for wireless transmissions. Mobile OSs were created specifically for mobile devices, such as a smartphone, tablet, or other embedded mobile OS. Two of the most popular OSs are Android OS (Google) and iPhone OS, or iOS (Apple). Wireless mobile computing refers to mobile computing without the need for wires or cables to connect to a network. The wireless system affords a fixed or portable end point with access to a distributed network. A distributed network consists of shared programming and data spread across more than one computer. A mobile computing system provides all the resources of that distributed network to devices that are portable, or that can go anywhere. However, because mobile systems are transported to various locations, they can experience issues within the locality that affect reception. Therefore, mobile and wireless systems actually achieve two different things. Wi-Fi is a wireless technology that allows electronic devices (e.g., smartphones, laptops, and tablets) to exchange data over the internet using radio waves by connecting to a Wi-Fi network in the vicinity or locale of the device. A Wi-Fi hotspot is a wireless access point that is usually provided in a public location, such as cafes, libraries, hotels, airports, and even grocery stores. Even though these technologies continue to improve, it is important to note that our mobile devices are only as secure as the network that we access and over which we transmit data.
Near field communication (NFC) and far-field communication refer to regions of the electromagnetic field around an object. NFC is a wireless and contactless communication technology that makes a device even smarter because it streamlines information transmissions and is the ultimate in connectivity. It allows the user to wave the smartphone over an NFC-compatible device to send information without having to touch the devices together or complete multiple steps to set up the connection. NFC-compatible devices contain an NFC tag that is passive and operates without a power supply of its own; it is designed to store information and transfer a wide variety of data types to other NFC-enabled devices. The architecture of the NFC tags evolved from radio-frequency identification (RFID). RFID uses radio waves to identify objects or people with encoded microchips. NFC tags are passive devices, and NFC chip technology operates as one part of a wireless link that, when activated by another chip, transfers data between the two devices. There are different types of NFC tags, including labels and wristbands with varying storage capacities and transfer speeds. Mobile computing applications will continue to evolve, and healthcare organizations will continue to meet the security challenge while they manage their mobile computing devices and wireless networks as enterprise solutions to meet their strategic plans.
Bandwidth, Broadband, and Mobile Broadband Versus Wireless Broadband ⬆ ⬇
Bandwidth and Broadband
Bandwidth is the measurement in bits, bytes, kilobytes, megabytes, and gigabytes of the data that can be transferred from or to your computer. Broadband, or a wide band or range of frequencies, is the minimum speed at which your connection will transfer information. Tundlam (2015) developed a simple analogy using roads and traffic to explain the difference between bandwidth and broadband. Bandwidth would be related to the “speed limit of the highway. Assuming each car is a fixed size, the number of cars going through a highway is nothing but the average speed of the cars on the highway. Cars per second would be the unit.” Tundlam likened broadband to the “highway itself. A fast lane that allows cars to go at a speed higher than on most other roads. Antonym is narrowband, analogous to a city road, much less speed and capacity.”
Mobile Broadband Versus Wireless Broadband
The difference between mobile and wireless broadband depends on the limitations of accessing the internet and the method of access.
Both wireless and mobile broadband are fast internet access technologies, but only mobile broadband permits end users to access the internet from different locations without restrictions. Some mobile broadband technologies are included in wireless broadband access methods because of the inaccessibility of wired connectivity.
Cloud Computing ⬆ ⬇
Cloud computing has web browser-based login-accessible data, software, and hardware that can be accessed and used. Using the cloud, systems can be linked together and costs reduced (Figure 3-4). According to Griffith (2020), cloud computing refers to storing and accessing data and programs over the internet, instead of on a computer's hard drive. “[T]he ‘cloud' is just a metaphor for the internet” (para. 3). According to Vennam (2020), the definition of cloud computing is as follows:
Figure 3-4 Cloud Computing
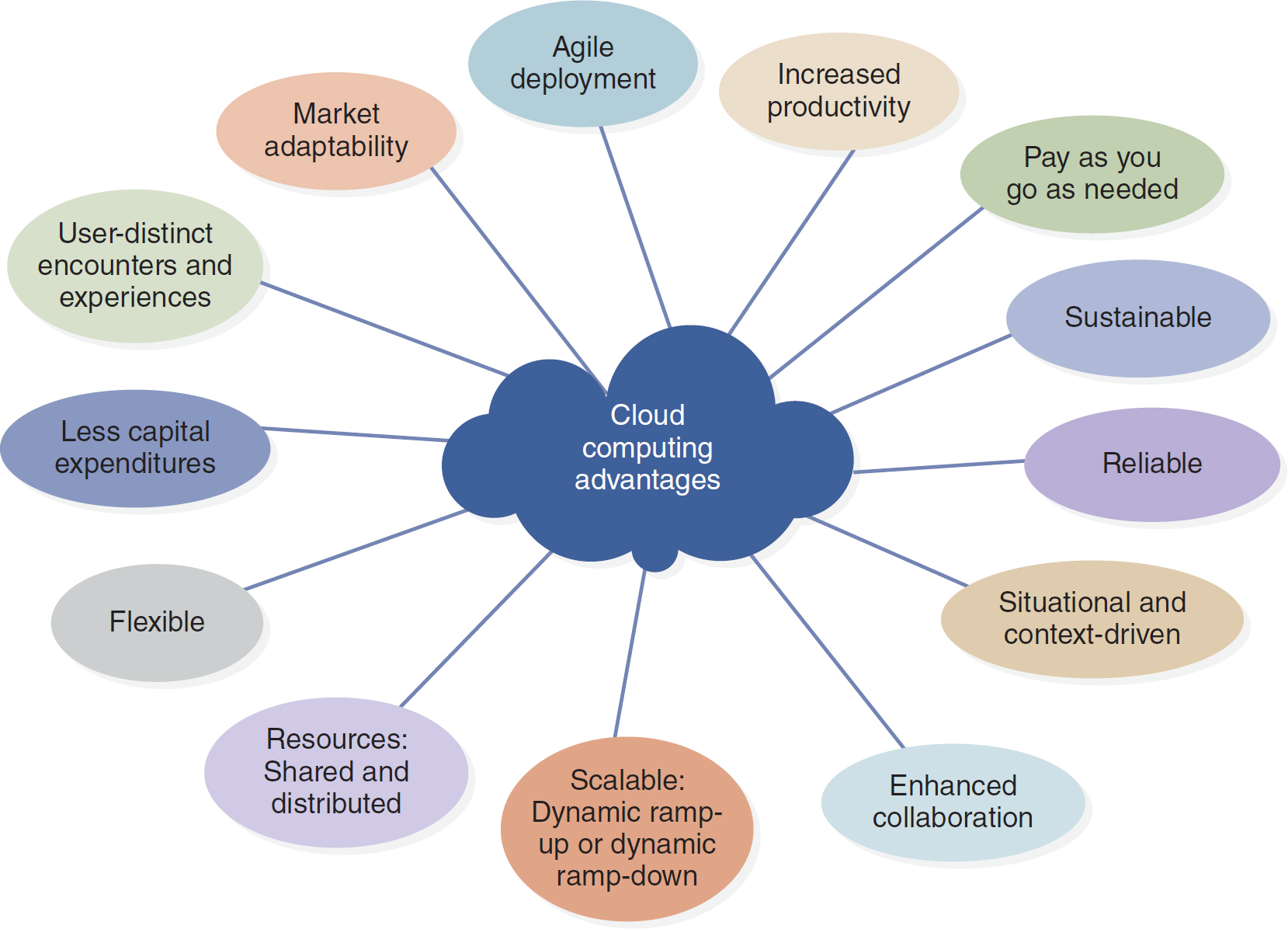
An illustration of a cloud lists the advantages of Cloud Computing.
The advantages include the following. Agile deployment; Increased productivity; Pay as you go as needed; Sustainable; Reliable; Situational and context-driven; Enhanced collaboration; Scalable with dynamic ramp-up or dynamic ramp-down; Resources are shared and distributed; Flexible; Less capital expenditures; User-distinct encounters and experiences; and Market adaptability.
[It] is on-demand access, via the internet, to computing resources-applications, servers (physical servers and virtual servers), data storage, development tools, networking capabilities, and more-hosted at a remote data center managed by a cloud services provider (or CSP). (para. 1)
The CSP is a pay as you go service, where the user is billed based on the resources they use. Robust technological capabilities such as artificial intelligence (AI) and blockchain technology are utilized to enhance security.
As we explore web-based apps and computing over the internet, we are cloud computing. Griffith (2020) described common examples of cloud computing that you might be using right now: Google Drive, Microsoft Office Online, Microsoft OneDrive, Apple iCloud, Amazon Cloud Drive, Box, Dropbox, and SugarSync. And then there's cloud hardware. The primary example of a device that is completely cloud centric is the Chromebook, which is a laptop that has just enough local storage and power to run the Chrome OS, which essentially turns the Google Chrome web browser into an operating system. The Chromebook moves cloud computing to the next level because applications and games accessed on the computer are executing on the cloud. Therefore, the Chromebook is an example of where personal computing might evolve-devices that have a web browser reaching out to online applications and services with a small number of local applications and minimal storage capabilities. In the cloud computing model, users must rely heavily on their internet providers for connectivity, speed, and bandwidth. The speed relates to how fast users can upload and download, and the bandwidth relates to how much data can be uploaded and downloaded. The speed and bandwidth issues could hinder mass appeal of the Chromebook. Cloud storage is the housing of data that is provided by networked online servers, which are typically located outside of the institutions whose data are being stored.
There are also services other than those already discussed that are based in the cloud and that are mainly business related: software as a service (SaaS), platform as a service (PaaS), and infrastructure as a service (IaaS) (Figure 3-5). SaaS, such as Salesforce.com, refers to cloud-based applications with the following benefits: quick start in using innovative or specific business apps that are scalable to a company's needs, any connected computer can access the apps and data, and data are not lost if a hard drive crashes because the data are stored in the cloud (Griffith, 2020; Vennam, 2020). PaaS provides everything needed to support the cloud application's building and delivery, which enables users to rapidly develop and launch custom web applications to the cloud (Griffith, 2020; Vennam, 2020). IaaS, such as Amazon, Microsoft, Google, and Rackspace, provide a rentable backbone to companies, enabling the scalable, on-demand infrastructure they need to support their dynamic workloads. Users pay for only what they use, and they do not have to invest in hardware, such as networks, storage, and data center space (Griffith, 2020; Vennam, 2020). Users can access and receive services from Netflix and Pinterest because they are customers of Amazon's cloud services. According to Precedence Research (2023), “The global cloud computing market size was valued at USD 446.51 billion in 2022 and is expected to hit USD 1,614.10 billion by 2030” (para. 1).
Figure 3-5 Software as a service (SaaS), platform as a service (PaaS), and infrastructure as a service (IaaS)
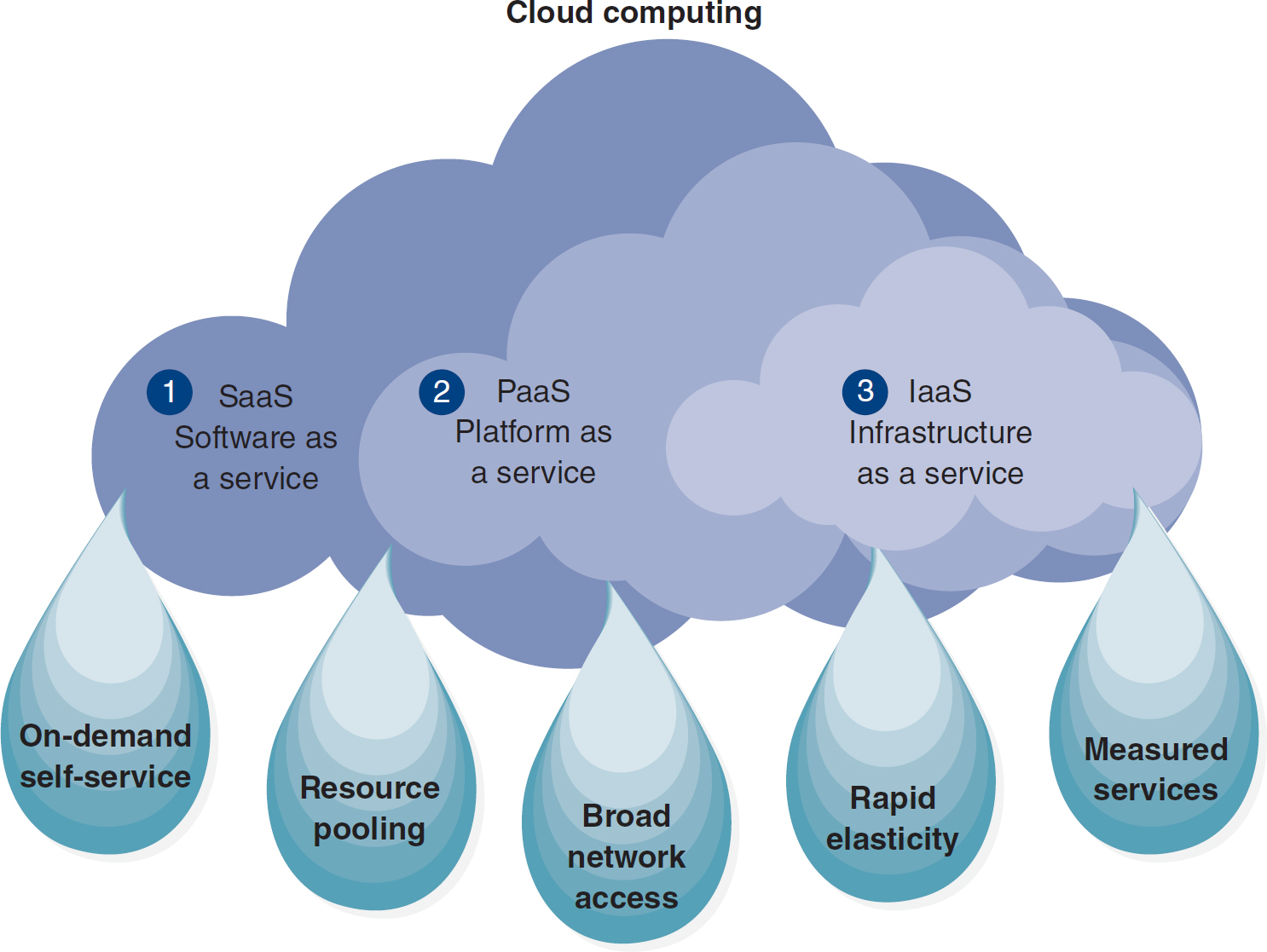
An illustration depicts the concept of cloud computing, emphasizing its service models and characteristics.
The illustration features three nested clouds pouring five water droplets. Clouds represent service models such as: 1. S a a S, software as a service; 2. P a a S, platform as a service; 3. I a a S, infrastructure as a service. Droplets represent key cloud computing characteristics, including on-demand self-service, resource pooling, broad network access, rapid elasticity, and measured services.
Cloud computing is internet computing, and it has the same pitfalls and benefits as using the internet. Some people are not sold on the claims that it is totally reliable, safe, and secure. Others believe it is a more environmentally friendly option because it uses fewer resources and less energy compared to other internet services, and yet many people can share efficiently managed, centralized cloud-based systems (Woodford, 2022). One of the driving forces behind the initiation of cloud computing was the need for affordable, scalable resources. As with anything on the internet, these resources can be shared or privately held. Cloud computing will continue to grow as long as there is a demand for it and it can meet the scalability requirements while maintaining secure, reliable spaces. Splunk (2022) stated that one of the top five security, incident, and event management (SIEM) priority trends to watch will continue to be cloud and app security. According to Doyle (2020), “Device-as-a-Service (DaaS) means medical teams can benefit from the more flexible provision of IT [information technology] equipment such as desktops, laptops and other mobile devices” (para. 1). Reflect on DaaS as one of the solutions in Case Study 3-1. What are the advantages of incorporating DaaS as one of the solutions in this health system?
| Case Study 3-1 |
|---|
| Hospital system: Mid-Cheshire Hospitals NHS Foundation Trust |
- 540 beds and community health services
- 4,500 staff across three hospital sites in northwest England
Problem: Aging infrastructure, including desktop devices that were over 10 years old, which was having a negative effect on thousands of its staff members' productivity and stressing its internal information technology help desk. Solution from CDW: Formulating a compelling business case and implementing the following: - Microsoft Office 365 to improve user experience; security, including email encryption; and support collaboration.
- Microsoft SharePoint platform for user collaboration.
- Windows 10 and new password reset tool to decrease help desk calls.
- Unable to replace all devices at once, CDW developed a business case to replace those devices over 10 years old; a DaaS solution delivered by CDW established a new 5-year refresh cycle.
Outcome: Infrastructure renewal is benefiting from CDW's CloudPlan service while CDW prepares for migration to Microsoft Azure* in the near future. CDW is also rolling out Cisco networking technology to enable free Wi-Fi for patients. *Microsoft described Azure as an “ever-expanding set of cloud services” (https://azure.microsoft.com/en-us/overview/what-is-azure). In the healthcare sector, McKesson, one of the oldest and largest healthcare companies, serving more than 50% of U.S. hospitals, chose Azure (https://cloud.netapp.com/blog/azure-cvo-blg-azure-case-studies-with-cloud-volumes-ontap). McKesson needed help to meet the infrastructure needs of their clients (https://cloud.netapp.com/hubfs/success-stories/CS-McKesson.pdf, para. 1). CDW. (n.d.). Case study: CDW helps Mid-Cheshire NHS Trust improve patient care by replacing ageing IT infrastructure. www.uk.cdw.com/about/case-studies/mid-cheshire-nhs-trust |
Realizing the benefits of using cloud computing is critical in health care as we seek to blend big data analytics with evidence-based practice to improve patient care. In an ideal world, nurses must be able to interact with computer technologies effectively to enhance patient care. They would be able to understand computer science and know how to harness its capabilities to benefit the profession and ultimately their patients.
Looking to the Future ⬆ ⬇
The use of the cloud will only continue to expand. The market for wearable technology, which comprises small handheld and portable computer systems and high-quality voice-activated inventions, will further facilitate the use of computers in nursing practice and professional development. The field of computer science will continue to contribute to the evolving art and science of nursing informatics. New trends promise to bring wide-ranging and (it is hoped) positive changes to the practice of nursing. Computers and other technologies have the potential to support a more client-oriented healthcare system in which clients truly become active participants in their own healthcare planning and decisions. Mobile health technology, telenursing, sophisticated electronic health records, and next-generation technology are predicted to contribute to high-quality nursing care and consultation within healthcare settings, including patients' homes and communities.
Computers are becoming more powerful and compact, which are factors that will contribute to the development of several technological initiatives that are currently evolving, such as quantum computing. Some of these initiatives are described here. These predicted innovations are only some of the many computer and technological applications being developed. As nurses gain proficiency in capitalizing on the creative, time-saving, and interactive capabilities emerging from information technology research, the field of nursing informatics will grow in similar proportions.
Quantum Computing
Quantum bits (qubits) are three-dimensional arrays of atoms in quantum states. A quantum computer is a proposed machine that is not based on the binary system but instead performs calculations based on the behavior of subatomic particles, or qubits. It is estimated that with quantum computing, we will be able to execute millions of instructions per second (MIPS) due to the qubits existing in more than one state at a time, or having the ability to simultaneously execute and process. According to Kennedy (2016), “the era of quantum computers is one step closer” (para. 1) due to the creation of qubits by David Weiss's (a professor of physics at Penn State University) research team.
Voice-Activated Communicators
Voice-activated communicators are already on the market, with new iterations being developed by a variety of companies, including Vocera Communications. Vocera (2019) developed the Vocera B3000n Communication Badge. This badge is a wearable, one-to-many, two-way, voice-controlled communication device. This device uses intuitive, simple commands to facilitate responses and communication permitting nurses to use wireless, hands-free devices to communicate with one another and to record data. Such technology is becoming a user-friendly and cost-effective way to increase clinical productivity.
Game and Simulation Technology
Game and simulation technology is offering immersive, realistic, innovative ways to teach content in general, including healthcare informatics concepts and skills. The same technology that powers video games is being used to create dynamic educational interfaces to help students learn about pathophysiology, care guidelines, and a host of other topics. Such applications are also valuable for client education and health promotion materials. The “serious games” industry is growing now that video game producers are looking beyond mere entertainment to address public and private policy; management; and leadership issues and topics, including those related to health care.
Virtual Reality and the Metaverse
VR is influencing and will continue to influence healthcare education and professional development. VR is a three-dimensional, computer-generated “world” in which a person (with the right equipment) can move about and interact as if they were actually in a physical location. The person's senses are immersed in this VR world using special gadgetry, such as head-mounted displays (HMDs), data gloves, joysticks, and other hand tools. Oculus Quest has become Meta Quest (www.meta.com/quest). The metaverse is an immersive world where our interactions are facilitated by the realities (virtual, augmented, and mixed), and we can move seamlessly from reality through VRs while we engage in our professional and personal lives. Headsets continue to evolve, and more are entering the market with greater capabilities and lighter weights and designs that will increase the amount of time people can wear them comfortably as the metaverse expands its reach into our personal and professional lives.
Mobile Devices
Mobile devices will be increasingly used by nurses, both at the point of care and in planning, documenting, interacting with the interprofessional healthcare team, and researching. Nurses will also be using such powerful wearable technologies as nano-based diagnostic sensors in their personal lives and will be generating their own data streams and receiving data from the wearable and mobile devices their patients use.
Mobile health (mHealth) is the use of mobile technologies, including mobile phones (and, increasingly, internet-enabled, wireless-connected smartphones), tablet computers and subnotebook microcomputers, remote diagnostic and monitoring devices, and global positioning system (GPS)/geographic information system (GIS) mapping equipment. As society becomes more mobile, people's medical, public health, and self-care health access and needs can be met with a set of apps, devices, and connections supported by their mobile devices.
Truly, data are at our fingertips.
Working Wisdom ⬆ ⬇
Since the beginning of the profession, nurses have applied their ingenuity, resourcefulness, and professional awareness of what works to adapt technology and objects to support nursing care, usually with the intention of promoting efficiency but also in support of client comfort and healing. This resourcefulness could also be applied effectively to the adaptation of information technology within the care environment, to ensure that the technology truly does serve patients, nurses, and the rest of the interprofessional team.
Consider this question: How can you develop competency in using the various computer hardware and software not only to promote efficient, high-quality nursing care and to develop yourself professionally but also to further the development of the profession's body of knowledge?
Application Scenario ⬆ ⬇
Dan P. has just been accepted into the nursing informatics graduate program. In the past, he has used his 8-year-old laptop to surf the World Wide Web, exchange email with friends, and play computer games. Now, however, Dan realizes that the computer is a vital tool for his academic success, and he has saved up enough money to purchase a new laptop computer and the necessary accessories he needs to be successful. He knows that his program will entail VR and that the university has launched their public metaverse space. What questions should he ask of his nursing advisor before he decides on the laptop he should purchase? Dan reached out to his nursing advisor, Dr. Smythely, and she sent Dan a list of general university and program-specific technical requirements needed for his success (see Box 3-3).
| Box 3-3 University and Program-Specific Technical Requirements |
|---|
| University General Technical Requirements |
|---|
| These requirements are designed to ensure your success. Please make sure that you are able to meet them, or consult with your student advisor or student support liaison.
As a student, you should be proficient using
|
- email,
- internet, and
- productivity software.
General Suggested Requirements* Laptop is required but a newer tablet (3 years old or less) and newer smartphone (3 years old or less) might be able to be used based on specific course requirements/needs. Suggested Setup* - Internet access is required and broadband is highly recommended.
- Windows Vista/7 or Mac OS X with virtualization software (such as Parallels with Windows OS)
- 2 GB of RAM minimum
- 40 GB hard drive
- Speakers connected to the computer
- Headphone connected to the computer
- All-in-one inkjet or laser printer
- Scanner or scanning application for mobile devices
- Portable media (thumb drive)
Software Requirements - Required web browser: Google Chrome in its most current version
- Microsoft Office
- Adobe
- Reader version 10.1 or higher
- Flash Player version 11.7 or higher
- Apple QuickTime version 7.7 or higher
- Windows Media Player version 11 or higher
- Antivirus software: Most current version of McAfee is suggested, but you can also use the most current version of Norton. This software must be installed, running, and kept current.
Additional Technology Requirements Specific programs or courses might require additional technologies that are not addressed in these general requirements. *These are the general requirements for the university, but you must consult the software/hardware requirements within your specific program of study with a faculty member, student advisor, or student support liaison. Please note that these recommendations and requirements may change as technology evolves, and changes could also vary from course to course throughout your program of study. |
| Nursing Informatics Graduate Nursing Program |
|---|
| Specific Technical Requirements in addition to the general requirements*
Laptop
|
MAC Minimum Requirements - Operating system: Mojave at a minimum; Big Sur would be maximum
- Processor: Intel i5 at least 2.0 GHZ
- Memory: 8 GB RAM or more
- Storage: 9 GB available space
- Graphics card: Dedicated GPU with minimum AMD Radeon Pro 560 4GB
- 2016 or newer hardware
- Microphone and webcam access
Minimum bandwidth: Bandwidth Requirements - 50 Kbps download per learner in the classroom, plus 16 Kbps per open mic learner (1 kbps = 0.001 Mbps)
- 200 Kbps upload (for your video feed) plus 900 Kbps to share your screen
Browser - Updated Chrome or Edge browser
Android Smartphone or Tablet Minimum System Requirements - Operating system: Android 7.1.1
- Processor: Qualcomm Snapdragon 835
- Memory: 4 GB RAM
- Storage: 5 GB available space
In addition to these specific technical requirements, you must meet the general requirements. |
After completing this chapter, how would you answer the following questions?
- Dan is set on purchasing a new laptop. Where is his money best spent and why? Would it be better to get the most memory, the fastest processor, the most storage, or the latest operating system?
- Dan is excited about VR but does not have a clue about which HMD would be best let alone how much they cost. Since he does not know anything about the headsets, what should he do to make an informed decision?
- Would you tell Dan to evaluate his internet speed and connectivity? How would you explain the importance of the terms broadband and bandwidth?
What else would you discuss with Dan before he chooses his laptop and HMD if he still wants to learn more about computers? You recommend that he review the following information: Brant (2023) and Burek (2023).
Summary ⬆ ⬇
The field of computer science is one of the fastest-growing disciplines. Astonishing innovations in computer hardware, software, and architecture have occurred over the past few decades, and there are no indications that this trend will come to a halt any time soon. Computers have increased in speed, accuracy, and efficiency yet now cost less and have reduced physical size compared to their forebears. These trends are predicted to continue. Current computer hardware and software serve as vital and valuable tools for both nurses and patients to engage in on-screen and online activities that provide rich access to data and information. Productivity, creativity, and communication software tools also enable nurses to work with computers to further foster knowledge acquisition and development. Wide access to vast stores of information and knowledge shared by others facilitates the emergence of wisdom in users, which can then be applied to nursing in meaningful and creative ways. It is imperative that nurses exploit the potential of the metaverse and become discerning yet skillful users of computer technology to apply the principles of nursing informatics to their practice to improve patient care and to contribute to the profession's ever-growing body of knowledge.
| Thought-Provoking Questions |
|---|
- How can knowledge of computer hardware and software help nurses to participate in information technology adoption decisions in the practice area?
- How can new computer software help nurses engage in professional development, collaboration, and knowledge dissemination activities at their own pace and leisure?
|
References ⬆
- Bithrey R. (2022, January 21). Best VR gloves 2022: Our top picks for virtual reality. VR Life. www.gfinityesports.com/vr/best-vr-gloves
- Brant T. (2023). The best desktop computers for 2023. PC Magazine. www.pcmag.com/picks/the-best-desktop-computers
- Burek J. (2023). The best computer mice for 2023. PC Magazine. www.pcmag.com/picks/the-best-computer-mice
- Doyle H. (2020, January 13). How DaaS can drive increased productivity in healthcare. CDW Blog. https://news.uk.cdw.com/how-daas-can-drive-increased-productivity-in-healthcare
- Evans D. (2019, June 24). Introduction to computing: Explorations in language, logic, and machines. http://computingbook.org/FullText.pdf
- Griffith E. (2020, June 29). What is cloud computing? PC Magazine. www.pcmag.com/news/what-is-cloud-computing
- Kennedy B. K. (2016, June 27). New, better way to build circuits for the world's first useful quantum computers. Phys.org. http://phys.org/news/2016-06-circuits-world-quantum.html#jCp
- Lyman P., & Varian H. R. (2003). How much information? 2003. Berkeley.edu. https://groups.ischool.berkeley.edu/archive/how-much-info-2003/printable_report.pdf
- Precedence Research. (2023). Cloud Computing Market Size to Surpass USD 1,614.10 BN by 2030. www.precedenceresearch.com
- SplunkTop 5 SIEM trends to watch in 2022.www.splunk.com/en_us/form/top-5-siem-trends.html
- Stegner B. (2022, February 12). How to use hand tracking on your Oculus Quest. Make Use Of. www.makeuseof.com/how-to-use-hand-tracking-oculus-quest
- Tundlam D. (2015, August 24). What is the difference between broadband and bandwidth? Quora. www.quora.com/What-is-the-difference-between-broadband-and-bandwidth
- UL Benchmarks. (2023). Best processors February 2023.https://aws.futuremark.com/compare/best-cpus
- Vennam S. (2020, August 18). What is cloud computing? IBM. web.archive.org/web/20221218040027/https://www.ibm.com/cloud/learn/cloud-computing
- Vocera. (2019). Data sheet: The B3000n Communication Badge. www.vocera.com/sites/default/files/2019-07/44_DS_B3000n_070119.pdf
- Woodford C. (2022, November 28). Cloud computing. Explain That Stuff. www.explainthatstuff.com/cloud-computing-introduction.html




