Objectives ⬇
- Assess processes for securing electronic information in a computer network.
- Identify various methods of user authentication and relate authentication to the security of a network.
- Consider methods for anticipating and preventing typical threats to network security.
Key Terms ⬆ ⬇
Introduction ⬆ ⬇
In addition to complying with the guidelines of the Health Insurance Portability and Accountability Act (HIPAA) and the Health Information Technology for Economic and Clinical Health (HITECH) Act regarding the privacy of patient information, healthcare systems need to be vigilant in the way they secure information and manage network security. Many have discussed and will continue to discuss the vulnerability of electronic health records to data breaches (Alder, 2021; McKeon, 2023; Mowry & Oakes, 2011). Mowry and Oakes (2011) suggested that as many as 77 people could view a patient's record during a hospital stay. One of the largest healthcare data breaches, over 3.5 million records, resulted from the hacking of a firewall vendor (Alder, 2021). Another third-party data breach was reported by McKeon (2023); this attack affected the information technology (IT) infrastructure and resulted in the loss of patient data since IT could not access or retrieve patient information. It is critical for IT policies and procedures to ensure appropriate access by clinicians and protect private information from inappropriate access. However, authentication procedures can be cumbersome and time-consuming, thus reducing clinicians' performance efficiency.
Physicians spend on average 7 minutes per patient encounter, with nearly 2 minutes of that time being devoted to managing logins and application navigation. Likewise, an average major healthcare provider must deal with more than 150 applications-most requiring different user names and passwords-which makes it difficult for caregivers to navigate and receive contextual information. Healthcare organizations must strike the right balance between simplifying access to core clinical data sets and maximizing the time providers can interact with patients without jeopardizing data integrity and security (Mowry & Oakes, 2011). AHIMA (n.d.) stated that “[d]ata quality and integrity requires consideration of privacy and security issues, including the protection of data against risks such as loss or unauthorized access, destruction, use, modification, or disclosures of data by parties not authorized to do so” (para. 7). This chapter explores the use of information and the processes for securing information in a health system computer network.
Securing Network Information ⬆ ⬇
Typically, a healthcare organization has computers linked together to facilitate communication and operations within and outside the facility. These linked computers are commonly referred to as a network. The linking of computers together and to the outside world creates the possibility of a breach of network security and exposes the information to unauthorized use. With the advent of smart devices, managing all these risks has become a nightmare for some institutions' security processes. In the past, stationary devices and computers resided within healthcare facilities. Today, smart devices travel in and out of healthcare organizations with patients, family members, and other visitors as well as employees-both staff and healthcare providers alike. Since wireless medical devices are becoming more advanced while being increasingly integrated into health care to enhance access and provide quality care, there are substantial security risks associated with their use. Medical devices such as insulin pumps and pacemakers must share data and information over the internet across networks and devices requiring that they are and remain cyber secure (Sullivan, 2012; U.S. Food and Drug Administration, 2022).
The three main areas of secure network information are confidentiality, availability, and integrity. An organization must follow a well-defined policy to ensure that private health information remains appropriately confidential. The confidentiality policy should clearly define which data are confidential and how those data should be handled. Employees also need to understand the procedures for releasing confidential information outside the organization or to others within the organization and know which procedures to follow if confidential information is accidentally or intentionally released without authorization. In addition, the organization's confidentiality policy should contain consideration for elements as basic as the placement of monitors so that information cannot be read by passersby. Shoulder surfing, which is watching over someone's back as that person is working, is still a major way that confidentiality is compromised.
Availability refers to network information being accessible when needed. This area of the policy tends to be much more technical in nature. An accessibility policy covers issues associated with protecting the key hardware elements of the computer network and the procedures to follow in case of a major electrical or internet outage. Food and drinks spilled onto keyboards of computer units, dropping or jarring hardware, and electrical surges or static charges are examples of ways that the hardware elements of a computer network may be damaged. In the case of an electrical outage or a weather-related disaster, the network administrator must have clear plans for data backup, storage, and retrieval. There must also be clear procedures and alternative methods of ensuring that care delivery remains largely uninterrupted.
Another way organizations protect the availability of their networks is to institute an acceptable use policy. Elements covered in such a policy could include which types of activities are acceptable on the corporate network. For example, are employees permitted to download music at work? Restricting downloads is a very common way for organizations to prevent viruses and other malicious code from entering their networks. The policy should also clearly define which activities are not acceptable and identify the consequences for violations.
The last area of information security is integrity. Employees must have confidence that the information they are reading is true. To accomplish this, organizations need clear policies to clarify how data are actually inputted, determine who has the authorization to change such data, and track how and when data are changed. All three of these areas use authorization and authentication to enforce the corporate policies. Access to networks can easily be grouped into areas of authorization (e.g., users can be grouped by job title). For example, anyone with the job title of “floor supervisor” might be authorized to change the hours worked by an employee, whereas an employee with the title of “patient care assistant” could not make such changes.
Authentication of Users ⬆ ⬇
Organizations also use authentication of employees in their security policies. The most common ways to authenticate a user rely on something the user knows, has, or is (Figure 12-1).
Figure 12-1 Ways to Authenticate Users: A. An ID Badge. B. Examples of Weak and Strong Passwords. C. A Finger on a Biometric Scanner.

A close-up shot of an identification badge worn on a person's chest. A label reads, Weak password: BobandSue; Strong password: M 2 f 4 hash e e g h forward slash. A person's index finger is on the verge of making contact with a biometric scanner.
A. © Photos.com. C. © Gary James Calder/Shutterstock, Inc.
Something a user knows is a password. Most organizations today enforce a strong password policy because free software available on the internet can break a password from the dictionary very quickly. Strong password policies include using combinations of letters; numbers; and special characters, such as plus signs (+) and ampersands (&). Some organizations are suggesting the use of passphrases to increase the strength of a password. See Box 12-1 for an overview of best practices for creating strong passwords. Policies typically include the enforcement of changing passwords every 30 or 60 days. Passwords should never be written down in an obvious place, such as a sticky note attached to the monitor or under the keyboard.
| Box 12-1 Best Practices for Creating and Managing Passwords |
|---|
| DO |
|---|
- Review the specific system guidelines for users; most of them will have information on password parameters and allowable characters.
- Use characters and symbols instead of letters, such as special characters (e.g., !, $, %, &, *).
- Create exclusive passwords for each account.
- Use longer passwords because they are harder to crack. Consider more than eight characters, and if the system allows, expand your password to 12 or 14 characters.
- Choose a password that is based on a phrase. Use portions or abbreviations of the words in the phrase, or use substitutions (e.g., $ for S, 4 for for) to create the password. For example, the phrase is “‘Lucy in the Sky with Diamonds' was released in 1967,” and the password is LUit$wdia67.
- Use at least four-word passphrases that seem obscure such as “kittens laugh bark catamaran.” This is easier to recall and less able to be hacked.
- After you create it, assess your password's strength if the site provides a password analyzer that will indicate its strength or weakness.
- Think carefully about the password, and create something that you will remember but that uses these different strategies to increase its strength.
- Change your password frequently, and do so immediately if you believe your system or email has been hacked. Some sites or organizations require you to change your password every 60 to 120 days. They also restrict how many recent passwords would not be able to be reused.
- Enable two-factor authentication, also referred to as multifactor authentication. Even if someone hacks your password, they would not be able to access your account if you also require a code to be sent to your phone. The hacker would then need your phone and your password.
- Use a password generator to obtain a randomized, more secure password.
- Consider using a password manager program to help you create strong passwords and store them securely.
- Check your username and password to see if your credentials were included in any recent data breaches using a security tool such as Have I Been Pwned? (https://haveibeenpwned.com).
|
| Do NOT |
|---|
- Share your password with anyone.
- Post your passwords in plain sight.
- Never use personal information such as your pet's name, phone number, address, bank account, or birthday. Avoid the birthdays of your significant others too.
- Use dictionary words.
- Use a string of numbers.
- Make simple changes to your old passwords, such as your current password being golf.players3 and your new password being golf.players4. It is best to create an entirely new password.
- Use keyboard strings or patterns that can be replicated such as fr5tghy6 or olp098.
- Use the same password for multiple sites.
Terwillegar, T. (2023, July 17). 10 essential password security best practices. Liquid Web. www.liquidweb.com/blog/password-security-best-practices |
The second area of authentication is something the user has, such as an identification (ID) card. ID cards can be magnetic, similar to a credit card, or have a radio-frequency identification (RFID) chip embedded into the card.
The last area of authentication is biometrics. Devices that recognize thumbprints or retina or facial patterns are available. Depending on the level of security needed, organizations commonly use a combination of these types of authentication.
Blockchain ⬆ ⬇
A blockchain is a digital database containing a record of transactions, maintained across several computers linked in a network, that can be simultaneously used and shared within a large, decentralized publicly accessible network. Transactions are logged publicly in chronological order. The database displays an ever-increasing list of ordered blocks; each block is time-stamped and connected to the block that came before it, thereby establishing a blockchain. Marr (2020) stated that a blockchain is a “super-secure method of storing, authenticating, and protecting data [that] could revolutionize many aspects of business-particularly when it comes to facilitating trusted transactions” (para. 7). It is important to note that each block cannot be altered, deleted, or otherwise modified since it is a permanent record that a given transaction has occurred. Blockchain technology lends itself well to the management of health records and proving identity, based on its security features. To provide multiple layers of security, healthcare organizations could restrict the connection points or network nodes in their communication network to only the HIPAA-covered entities, encrypt some data, and leave other data off blockchain (Alder, n.d.; Miliard, 2017). Visibility and accountability are strengths, but it is important to note that not all blockchains must be publicly available.
| Blockchain Applications in Health Care |
|---|
| Healthcare research could be facilitated by blockchain technology since the technology could generate a layer of de-identified data that researchers could access. Blockchain technology could enact patient-centered care by positioning the patient at the center of the healthcare delivery system while improving privacy, security, and interoperability.
Healthcare settings have numerous ways to enter the patient's date of birth, and the date cannot be standardized after it has been entered. Blockchain can be used in this case by linking patients to their data instead of to their identity. Blockchain can also conduct identity management of the healthcare provider.
|
Use Case for Blockchain Technology ⬆ ⬇
A use case describes a distinct situation in which a specific product or service could possibly be used. The following use case focuses on blockchain technology.
Blockchain Use Case: Insurance Claim Processing
The goal of this use case was to automate health insurance claim processing by demonstrating the application of blockchain to the insurance industry and specifically in health care. Blockchain technology maintains the patient's privacy while allowing data to be shared between entities in a synchronized and secured process. The benefits of using blockchain include improved efficiency, better trust and control, faster claims processing, smart contract capabilities, and fraud prevention. Using blockchain in health care “can reduce the costs and inefficiencies associated with processing and paying healthcare claims, thereby combating fraudulent activities. Blockchain can reduce the time needed to process claims by storing data and automating the validation process” (Gyan Solutions, 2023, para. 16).
Preauthorization payment claim transactions must be verifiable and smart contract-enabled distributed ledger technology (DLT) leveraged. DLT is a technological infrastructure with protocols to simultaneously access, validate, record, share, coordinate, and synchronize transactions in electronic ledgers across a network that spans numerous entities or locations. DLT has already succeeded in the financial technology industry.
Blockchain use cases, such as the one described, reveal the following benefits of blockchain technology:
- Decentralized management
- Indisputable audit trail
- Data trusted, transparent, and easily tracked
- Robustness and availability
- Privacy and security
Threats to Security ⬆ ⬇
The largest benefit of a computer network is the ability to share information. However, organizations need to protect that information and ensure that only authorized individuals have access to the network and the data appropriate to their role. Threats to data security in healthcare organizations are becoming increasingly prevalent. A nationwide survey by the Computing Technology Industry Association (CompTIA) found that human error was responsible for more than half of security breaches. Human error was categorized as failure to follow policies and procedures, with more than half of the organizations believing that their employees ignore their cybersecurity guidelines, are generally careless, lack experience with websites and applications, and are unaware of new threats (Greenberg, 2015; O'Driscoll, 2023). The literature continues to abound with information concerning the snowballing volume of electronic patient data that is vulnerable and the frequency and types of compliance complaints and data breaches such as hacking, loss, improper handling, and theft (Alder, 2021; American Hospital Association, 2023b; Culbertson, 2021; DeGaspari, 2010; Health Information and Management Systems Society [HIMSS], 2019).
In the Fifth Annual Benchmark Study on Privacy and Security of Healthcare Data, the Ponemon Institute (2015) reported that “[m]ore than 90 percent of healthcare organizations represented in this study had a data breach, and 40 percent had more than five data breaches over the past two years” (para. 3). Interestingly, the most common type of data breach was related to a criminal attack on the healthcare organization (up 125% over the past 5 years). Key terms related to criminal attacks are brute force attack (i.e., software used to guess network passwords) and zero day attack (i.e., searching for and exploiting software vulnerabilities). Of the intentional data breaches (as opposed to unintentional), “45 percent of healthcare organizations say the root cause of the data breach was a criminal attack and 12 percent say it was due to a malicious insider” (Ponemon Institute, 2015, para. 4). That leaves nearly 43% of data breaches in the unintentional category. Alder (2015) reported on the HIMSS 2015 Healthcare Cybersecurity Survey, which determined the negligent insider to be the most common source of a security breach. Examples of unintentional, or negligent, breaches include lost or stolen devices and walking away from a workstation without logging off, both of which could be cause for discipline or even dismissal from a job. An interesting example of an unintentional data breach was reported on the Office for Civil Rights website. A company leased photocopier equipment and returned it without erasing the healthcare data stored on the copier's hard drive, which resulted in a settlement of over $1.2 million (U.S. Department of Health and Human Services [HHS], 2017). The findings of the 2019 HIMSS Cybersecurity Survey suggested that “healthcare cybersecurity practices are moving in the right direction with some degree of uniformity. The findings also suggest there is room for improvement” (p. 20). Alder (2020) stated that “2019 was a particularly bad year for healthcare data breaches with 510 data breaches reported by HIPAA-covered entities and their business associates. That equates to a rate of 42.5 data breaches per month” (para. 2). There was a major increase in hacking and IT incident breaches: “[M]ore than 59% of data breaches reported to the HHS' Office for Civil Rights were the result of hacking, malware, ransomware, phishing attacks, and other IT security breaches” (Alder, 2020, para. 4). According to Alder (2021), “Across the 686 2021 healthcare data breaches, 44,993,618 healthcare records have been exposed or stolen, which makes 2021 the second-worst year in terms of breached healthcare records” (para. 3). The worst year thus far has been 2020 (Kath, 2021). We are improving but must maintain and increase our efforts. Recurring security training for employees can help reduce the risks associated with phishing attacks, and healthcare organizations must be proactive in anticipating the potential for and preventing security breaches.
The first line of defense is strictly physical. A locked office door, an operating system that locks down after 5 minutes of inactivity, and regular security training programs are extremely effective in this regard. Proper workspace security discipline is a critical aspect of maintaining security. Employees need to be properly trained to be aware of computer monitor visibility, shoulder surfing, and policy regarding the removal of computer hardware. A major issue facing organizations is removable storage devices (Figure 12-2). Jump drives, flash drives, and thumb drives (which use USB port access) are potential security risks. These devices can be slipped into a pocket and therefore easily removed from the organization. One way to address this physical security risk is to limit the authorization to write files to a device. Organizations are also turning off the USB ports on company desktops.
Figure 12-2 A Removable Storage Device

A person's hand places a U S B storage device into a computer system.
© Alex Kotlov/Shutterstock, Inc.
The most common security threats a corporate network faces are hackers, malicious codes (i.e., spyware, adware, ransomware, viruses, worms, and Trojan horses), and malicious insiders. Acceptable use policies help to address these problems. For example, employees may be restricted from downloading files from the internet. Downloaded files, including email attachments, are the most common way viruses and other malicious codes enter a computer network. Typically, network security policies prohibit employees from using personal USB drives, thereby preventing the transfer of malicious codes from a personal computer to the network.
Let's look more closely at some of these common network security threats. Typically, we think of hackers as outsiders who attempt to break into a network by exploiting software and network vulnerabilities, and indeed these black hat (i.e., malicious) hackers (also called crackers) do exist. However, more organizations are looking to employ ethical hackers (i.e., white hat hackers), who are the hackers skilled at looking for and closing network security vulnerabilities (Caldwell, 2011; Milijkovac, 2022).
Spyware and adware are normally controlled in a corporate network by limiting the functions of the browsers used to surf the internet. For example, browser privacy options can control how cookies are used. A cookie is a very small file written to the hard drive of a computer whose user is surfing the internet. This file contains information about the user. For example, many shopping sites write cookies to the user's hard drive containing the user's name and preferences. When that user returns to the site, the site will greet them by name and list products in which they are possibly interested. Weather websites send cookies to users' hard drives with their ZIP code so that when a user returns to that site, the local weather forecast is immediately displayed. On the negative side, cookies can follow the user's travels on the internet. Marketing companies use spying cookies to track popular websites that could provide a return on advertising expenditures. Spying cookies related to marketing typically do not track keystrokes in an attempt to steal user IDs and passwords; instead, they simply track which websites are popular, and these data are then used to develop advertising and marketing strategies. Nurse informaticists exploring new healthcare technologies on the internet may find that ads for these technologies begin to pop up the next few times they are on the internet. Spyware that does steal user IDs and passwords contains malicious code that is normally hidden in a seemingly innocent file download. This threat to security explains why healthcare organizations typically do not allow employees to download files. The rule of thumb to protect the network and one's own computer system is to download files only from a reputable site that provides complete contact information. Be aware that sometimes malicious code is hidden in an email link or in a file sent by a trusted contact whose email has been hacked. If you are not expecting a file from an email contact or if you receive an email with only a link in it, resist the urge to download or click.
A relatively new threat to healthcare organizations is ransomware, which is malicious code that blocks the organization from using its computer systems until a ransom is paid to the hacker. Business Wire (2021) suggested that healthcare delivery systems must pay attention to the Ponemon Institute's research concerning ransomware and transform their current cybersecurity practices. The American Hospital Association (2023a) reported that the FBI “seized control of servers and websites used by the Hive ransomware network to target hospitals and other critical infrastructure, and infiltrated the network in July to provide decryption keys to victims and prevent $130 million in ransom payments” (para. 1). Consider the following cases of ransomware intrusion from 2016 and 2020. Waddell (2016) described a hospital in Los Angeles that operated without access to its electronic health records for several weeks when hackers took over its computer systems and then demanded $3.6 million in bitcoin cryptocurrency ransom to return access of the computer system to the hospital. Cryptocurrencies provide anonymity to the hackers. The hackers were able to encrypt the patient records, which meant even though they might not have gained access to the files, the real goal was not to access the content of these records but instead to hold them hostage so that the hospital could not access them. This ransom was made possible due to ransomware, which is viruses and malware unleashed to take over a server or computer by encrypting the files so that hackers can demand money to return control to the rightful owners. With the expanding use of networked devices and servers, hackers are leveraging ransomware attacks because businesses must have access to their data. Such attacks continue to affect healthcare organizations and have even interfered with clinical trials. Perlroth (2020) reported on October 3, 2020, that in the past 2 weeks, a company that “sells software used in hundreds of clinical trials, including the crash effort to develop tests, treatments and a vaccine for the coronavirus, was hit by a ransomware attack that has slowed some of those trials” (para. 1). These attacks can be devastating and far-reaching; this company's software is being used in pharmaceutical trials conducted throughout Europe, Asia, and North America.
In addition to strict policies related to network security, organizations may also use software or hardware tools, such as firewalls (covered in the next section) and intrusion detection devices, to protect from hackers. Protect yourself at home by ensuring that you have an updated version of antivirus software, be wary of unusual emails, and develop strong passwords and change them frequently. If your email is hacked, report it to the proper authorities as soon as possible, warn your contacts that you have been hacked, change your password, and check to see that your antivirus software is up to date.
Another huge threat to corporate security is social engineering, which is the manipulation of a relationship based on one's position (or pretend position) in an organization. For example, someone attempting to access a network might pretend to be an employee from the corporate IT office who simply asks for an employee's user ID and password. The outsider can then gain access to the corporate network. Once this access has been obtained, all corporate information is at risk. A second example of social engineering is a hacker impersonating a federal government agent. After talking an employee into revealing network information, the hacker has an open door to enter the corporate network. A related type of social engineering is phishing, which is an attempt to steal information by manipulating the recipient of an email or phone call to provide passwords or other private information. Box 12-2 contains an example of a phishing email and tips for identifying phishing scams.
| Box 12-2 Identifying Phishing Scams |
|---|
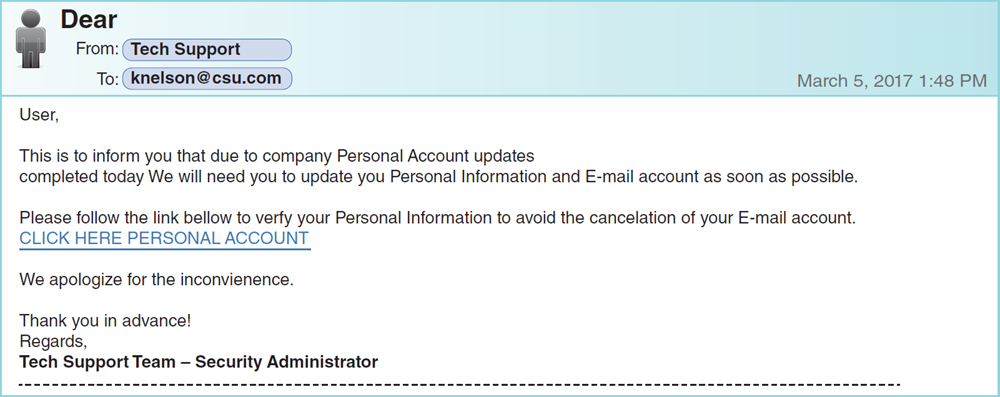 The information in the email, including spelling and grammar errors, is as follows. Dear, From: Tech Support. To: nelson, misspelled as k n e l s o n, at c s u dot com. Dated March 5, 2017 1:48 pm. User, This is to inform you that due to company Personal Account updates completed today We will need you to update you Personal Information and E-mail account as soon as possible. Please follow the link bellow to verify, misspelled as v e r f y, your Personal Information to avoid the cancelation of your E-mail account. CLICK HERE PERSONAL ACCOUNT. We apologize for the inconvenience, misspelled as i n c o n v i e n e n c e. Thank you in advance! Regards, Tech Support Team - Security Administrator. Under the head Example of a Phishing Scam Email, the text reads as follows. Check suspicious emails for grammar and spelling errors, generic greetings, for example, User, Dear, or Dearest, or requests for immediate action or personal information, for example, passwords or bank account numbers. Some phishing emails may appear to come from your bank or another trusted organization. Think carefully about why a seemingly legitimate organization might be asking for information it should already have or why it might need to know what it is asking for. Be aware of your organization's procedures for reporting phishing scams, and do so immediately. Source line reads, Data from: Pennsylvania State University, Office of Information Security. No date. What is phishing? h t t p colon double forward slash phishing dot p s u dot e d u forward slash what hyphen is hyphen phishing. |
| Example of a Phishing Scam Email |
|---|
| Check suspicious emails for grammar and spelling errors, generic greetings (e.g., User, Dear, or Dearest), or requests for immediate action or personal information (e.g., passwords or bank account numbers). Some phishing emails may appear to come from your bank or another trusted organization. Think carefully about why a seemingly legitimate organization might be asking for information it should already have or why it might need to know what it is asking for. Be aware of your organization's procedures for reporting phishing scams, and do so immediately.
Data from: Pennsylvania State University, Office of Information Security. (n.d.). What is phishing? http://phishing.psu.edu/what-is-phishing
|
Additional types of social engineering schemes include spear phishing, which is a more specifically targeted scheme whereby the attacker takes advantage of contact information provided in an organization's directory and tailors the scam email to a specific person; baiting, which is when a malware-infected USB flash drive is left in a public area, thus tricking the finder into loading it to identify its owner; and scareware, which is when the scam email reports that the user has been hacked and tricks them into giving the hacker remote access to the computer to “fix” it (Rosencrance, n.d.).
Another example of an important security threat to a corporate network is the malicious insider. This person can be a disgruntled or recently fired employee whose rights of access to the corporate network have not yet been removed. In the case of a recently fired employee, their network access should be suspended immediately upon notice of termination. To avoid the potentially hazardous issues created by malicious insiders, healthcare organizations need a policy and specific procedures to monitor employee activity to ensure that employees carry out only those duties that are part of their normal job. Separation of privileges is a common security tool, which means that no single employee should be able to complete a task that could cause a critical event without the knowledge of another employee. For example, the employee who processes and prints the checks should not be the same employee who signs those checks. Similarly, the employee who alters pay rates and hours worked should be required to submit a weekly report to a supervisor before the changes take effect.
Software that can track and monitor employee activity is also available. This software can log which files an employee accesses and whether changes were made to the files or the files were copied. Depending on the number of employees, organizations may also employ a full-time electronic auditor who does nothing but monitor activity logs and hire full-time employees to provide network security. The amount of money allocated varied greatly, but “over one-quarter of respondents (26%) operate within a system that spends money on cybersecurity activities/resources, even though there is no specific cybersecurity ‘carve out' within the IT budget” (HIMSS, 2019, p. 9). Additional strategies for securing networks that were suggested in this HIMSS survey were mock cyber defense exercises, sharing information between and among healthcare organizations, monitoring vendor intelligence feeds, and subscribing to security alerts and tips from the United States Computer Emergency Readiness Team (www.cisa.gov).
Security Tools ⬆ ⬇
A wide range of tools is available to an organization to protect the organizational network and information. Software Testing Help (2023) provides cybersecurity testing tools for mobile devices to the web, including antivirus technology, firewalls, and data encryption being used in health care. These tools can be either a software solution, such as antivirus software, or a hardware tool, such as a proxy server. Such tools are effective only if they are used along with employee awareness training.
For example, email scanning is a commonly used software tool. All incoming email messages are scanned to ensure that they do not contain a virus or some other malicious code. This software can find only viruses that are currently known, so it is important that the virus software be set to search for and download updates automatically. Organizations can further protect themselves by training employees to never open an email attachment unless they are expecting the attachment and know the sender. Even IT managers have fallen victim to email viruses that sent infected emails to everyone in their address book. Employees should be taught to protect their organization from new viruses that may not yet be included in their scanning software by never opening an email attachment unless the sender is known and the attachment is expected. Email scanning and antivirus software should never be turned off, and updates should be installed at least weekly or, ideally, daily. Software is also available to scan instant messages and automatically delete spam email.
Many antivirus and adware software packages are available for fees ranging from free to more than $25 per month (for personal use) to several thousands of dollars per month (to secure an organization's network). The main factors to consider when purchasing antivirus software are its effectiveness (i.e., the number of viruses it has missed), the ease of installation and use, the effectiveness of the updates, and the help and user support available. Numerous websites compare and contrast the most recent antivirus software packages. Be aware, however, that some of these sites also sell antivirus software, so they may present biased information.
Firewalls are another tool used by organizations to protect their corporate networks when they are connected to the internet. A firewall can be hardware or software or a combination of both and is used to examine all incoming messages or traffic to the network. The firewall can be set up to allow only messages from known senders into the corporate network and look at outgoing information from the corporate network. If the message contains some type of corporate secret, the firewall may prevent the message from leaving. In essence, firewalls serve as electronic security guards at the gate of the corporate network.
Proxy servers also protect the organizational network by preventing users from directly accessing the internet. Instead, users must first request passage from the proxy server. The server looks at the request and makes sure that the request is from a legitimate user and that the destination of the request is permissible. For example, organizations can block requests to view a website with the word sex in the title or the actual uniform resource locator of a known pornography site. The proxy server can also lend the requesting user a mask to use while they are surfing the web, which allows the corporation to protect the identity of its employees. The proxy server keeps track of which employees are using which masks and directs the traffic appropriately.
With hacking becoming more common, healthcare organizations must have some type of protection to avoid this invasion. An intrusion detection system (both hardware and software) allows an organization to monitor who is using the network and which files that user has accessed. Detection systems can be set up to monitor a single computer or an entire network. Corporations must diligently monitor unauthorized access of their networks. Anytime someone uses a secured network, a digital footprint of all the user's travels is left, which can be easily tracked by electronic auditing software.
Everyone in nursing informatics and IT has a tremendous amount of work to do and must be forever vigilant to maintain the highest level of cybersecurity. Healthcare organizations have taken many positive steps since the 2015 HIMSS survey, which is reflected in the 2019 survey. In 2019, 44% of the respondents agreed and 15% strongly agreed that “[c]ybersecurity professionals feel empowered to drive change in healthcare organizations” (HIMSS, 2019, p. 8). The 2021 HIMSS Cybersecurity Survey reflected that “most respondents (59%) reported an increase in cybersecurity budgets for 2022. It is likely that this increase in budgets will lead to more positive growth within healthcare cybersecurity programs” (HIMSS, 2022, p. 15).
Off-Site Use of Portable Devices ⬆ ⬇
Off-site use of portable devices, such as laptops, tablets, home computing systems, smartphones, smart devices, and portable data storage devices, can help to streamline the delivery of health care. For example, home health nurses may need to access electronic protected health information (EPHI) via a wireless laptop connection during a home visit, or a physician might use a smartphone to get specific patient information related to a prescription refill in response to a patient request. These mobile devices are invaluable to healthcare efficiency and responsiveness to patient need in such cases. At the very least, however, agencies should require data encryption when EPHI is being transmitted over unsecured networks or transported on a mobile device as a way of protecting sensitive information. Hotspots provided by businesses, such as coffee shops or restaurants and airports, are not secured networks. Virtual private networks (VPNs) must be used to ensure that all data transmitted on unsecured networks are encrypted. The user must log in to the VPN to reach the organization's network.
Only data essential for the job should be maintained on a mobile device; other nonclinical information, such as Social Security numbers, should never be carried outside the secure network. Some institutions make use of thin clients, which are basic interface portals that do not keep secure information stored on them. Essentially, users must log in to the network to get the data they need. Use of thin clients may be problematic in patient-care situations where the user cannot access the network easily. For example, some rural areas of the United States do not have wireless or cellular data coverage. In these instances, private health information may need to be stored in a clinician's laptop or tablet. This is comparable to home health nurses carrying paper charts in their cars to make home visits and entails the same responsibilities that accompany such use of private information outside the institution's walls.
What happens if one of these devices is lost or stolen? The agency is ultimately responsible for the integrity of the data contained on these devices and is required by HIPAA regulations (HHS, 2006) to have policies in place covering such items as appropriate remote use, removal of devices from their usual physical location, and protection of these devices from loss or theft. Simple rules, such as covering laptops left in a car and locking car doors during the transport of mobile devices containing EPHI, can help to deter theft. If a device is lost or stolen, the agency must have clear procedures in place to help ensure that sensitive data are not released or used inappropriately. Software packages that provide for physical tracking of the static and mobile computer inventory, including laptops, smartphones, and tablets, are being used more widely and can assist in the recovery of lost or stolen devices. In addition, some software that allows for remote data deletion (data wipe) in the event of theft or loss of a mobile device can be invaluable to the agency in preventing the release of EPHI.
If a member of an agency is caught accessing EPHI inappropriately or stealing a mobile device, the sanctions should be swift and public. Sanctions may range from a warning or suspension with retraining to termination or prosecution, depending on the severity of the security breach. The sanctions must send a clear message to everyone that protecting EPHI is serious business. The following strategies for managing remote access are imperative:
- Remote access must be restricted to company-owned and company-configured computers and devices.
- Strong VPN policies must be in place and enforced, including the creation of a safe space or sandbox that isolates or quarantines the session from other software running on the remote device.
- User privileges associated with remote access must be stringently applied and enforced based on company policy.
- Effective educational programming must be instituted and mandated for all personnel to ensure safe computing practices associated with remote locations and remote access. Updates and retraining must be provided at specified intervals to maintain safe remote access practices.
To protect patients and their data, nurses must consider the effect of wireless mobile devices (see Box 12-3). Data can be stolen by an employee very easily through the use of email or file transfers.
| Box 12-3 Pokemon Targets Hospital |
|---|
| Informatics nurse specialists must be aware of the uses of portable devices. In 2016, this came to light when one hospital in the Pittsburgh area was a site of a popular game and the administration was upset because it created a privacy issue for people using their hospital as a search site. This hospital contacted the game developer to be removed from its game.
Hospitals must always be concerned about privacy and safety issues within their control but also be on the alert for those outside their control, such as the Pokemon Go game. Marcie Cipriani, with Pittsburgh's Action News 4, reported that Pokemon Go used West Penn Hospital, which is part of the Allegheny Health Network in Pittsburgh, as a real-world location in the game. The game utilizes enhanced reality, which allows players to combine images from the real world with those of the game. The Allegheny Health Network officials stated that the exciting, interactive game created concerns when it brought players inside their hospital. They say hunting Pokemon at the hospital created a patient privacy issue and a safety concern. Administrators warned those who were playing to stay out of their hospitals, and they contacted the game's developer, who agreed to remove their hospitals from the app. They asked their employees to be on the lookout for anyone playing the app while they were walking around the hospital and to contact security if they saw Pokemon Go players.
Data from: Cipriani, M. (2016, July 29). Pokemon ‘Gone:' Players banned from Allegheny Health Network facilities. Pittsburgh's Action News 4. www.wtae.com/article/pokemon-gone-players-banned-from-allegheny-health-network-facilities-1/7481333
|
Malware, or malicious code, that infiltrates a network can collect easily accessible data. One of the evolving issues is lost or stolen devices that can provide a gateway into a healthcare organization's network and records. When the device is owned by the employee, other issues arise as to how the device is used and secured.
The increase in cloud computing has also challenged healthcare professionals' personal and professional security and privacy. Cloud computing refers to storing and accessing data and computer programs on the internet rather than on the local hard drive of a computer. Common examples of cloud computing for personal use include Google Drive, Apple iCloud, and Amazon. Cloud computing allows for easy syncing of separate devices to promote sharing and collaboration (Griffith, 2022). According to Jansen and Grance (2011), cloud computing “promises to have far-reaching effects on the systems and networks of federal agencies and other organizations. Many of the features that make cloud computing attractive, however, can also be at odds with traditional security models and controls” (p. vi). Healthcare organizations moved to the cloud because cloud computing tends to be cheaper and faster, offers more flexibility for work location, provides nearly immediate disaster recovery, supports collaboration, provides security, and offers frequent software updates (Salesforce UK, 2020). However, there are important security concerns related to cloud computing in health care. To maintain security in a cloud environment, several safeguards must be in place, such as encoding files with encryption at both the local and the cloud levels, adding multiple access controls such as multifaceted authentication methods, and providing data loss prevention (DLP) protocols and tools. The threats continue. According to Accenture (n.d.), “digitalization and the Cloud Continuum have redefined not only enterprise boundaries and capabilities but also the attack surface, adding vulnerabilities that are beyond the reach of traditional responses” (para. 2). Therefore, data must be guarded as more and more functions are moved to the cloud. One way to do this is through the DLP strategy. This approach is critical for making sure that end users do not send sensitive or critical information outside the institution's network. The virtual desktop interface (VDI) allows the user to have a computer for which the operating system, applications, and data are located and accessed on a central server instead of on the local desktop. Many VDIs are cloud based, meaning a complete desktop and app virtualization service runs in the cloud. Desktops can have security issues, but with the VDI, the IT team can generate and delete virtual desktops instantly. On the flip side, the cloud must then be secured.
It is clear that healthcare organizations need to be extra vigilant about their data security when using cloud computing. However, as we emphasized several times in this chapter, employee training on security measures may be the most important defense. Many security strategies are focusing on employees or threats from within since careless or negligent employees are still considered a major risk to the healthcare organization (Ekran, 2023; Guccione, 2015; Schwartz, 2022).
Summary ⬆ ⬇
Technology changes so quickly that even the most diligent user will likely encounter a situation that could constitute a threat to their network. Organizations must provide their users with the proper training to help them avoid known threats and, more importantly, be able to discern a possible new threat. Consider that 10 years ago wireless networks were the exception to the rule, whereas today access to wireless networks is almost taken for granted. How will computer networks be accessed 10 years from now? The most important concept to remember from this chapter is that the only completely safe network is one that is turned off. Network accessibility and network availability are necessary evils that pose security risks. The information must be available to be accessed, yet it must remain secured from hackers, unauthorized users, and any other potential security breaches. As the cloud expands, so do the concerns over security and privacy. The major threat remains from insiders or employees being negligent or malicious. In an ideal world, everyone would understand the potential threats to network security and diligently monitor and implement tools to prevent unauthorized access of their networks, data, and information.
| Thought-Provoking Questions |
|---|
- Sue is a chronic obstructive pulmonary disorder clinic nurse enrolled in a master's education program. She is interested in writing a paper on the factors that are associated with poor compliance with medical regimens and associated repeat hospitalization of chronic obstructive pulmonary disorder patients. She downloads patient information from the clinic database to a thumb drive that she later accesses on her home computer. Sue understands rules about privacy of information and believes that because she is a nurse and needs this information for a graduate school assignment, she is entitled to the information. Is Sue correct in her thinking? Describe why she is or is not correct.
- The nursing education department of a large hospital system has been centralized; as a consequence, the nurse educators are no longer assigned to one hospital but must now travel among all the hospitals. They use their smartphones to interact and share data and information. What are the first steps you would take to secure these transactions? Describe why each step is necessary.
- Research cloud computing in relation to health care. What are the major security and privacy challenges? Please choose three and describe them in detail.
- Blockchain is touted as a security measure. Describe in detail how blockchain technology functions and why it would help maintain security.
- How can organizations decrease negligence among their employees? State two detailed ways to prevent breaches caused by careless employees.
|
References ⬆
- Accenture. (n.d.). Cybersecurity as competitive advantage in a world of uncertainty.www.accenture.com/us-en/services/security-index
- AHIMA. (n.d.). AHIMA policy statement: Data quality and integrity.www.ahima.org/advocacy/policy-statements/data-quality-and-integrity
- Alder S. (n.d.). HIPAA encryption requirements. HIPAA Journal. www.hipaajournal.com/hipaa-encryption-requirements
- Alder S. (2015, July 9). HIMSS releases 2015 healthcare cybersecurity report. HIPPA Journal. www.hipaajournal.com/himss-releases-2015-healthcare-cybersecurity-report-8014
- Alder S. (2020, February 21). January 2020 healthcare data breach report. HIPAA Journal. www.hipaajournal.com/january-2020-healthcare-data-breach-report
- Alder S. (2021, December 30). Largest healthcare data breaches of 2021. HIPAA Journal. www.hipaajournal.com/largest-healthcare-data-breaches-of-2021
- American Hospital Association. (2023a, January 26). FBI disrupts ransomware network targeting hospitals and others.www.aha.org/news/news/2023-01-26-fbi-disrupts-ransomware-network-targeting-hospitals-and-others
- American Hospital Association. (2023b, February 21). OCR: HIPAA breaches down, compliance complaints up in 2021.www.aha.org/news/headline/2023-02-21-ocr-hipaa-breaches-down-compliance-complaints-2021
- Business Wire. (2021, September 22). New Ponemon Institute research shows ransomware attacks on healthcare delivery organizations can lead to increased mortality rate.www.businesswire.com/news/home/20210922005436/en/New-Ponemon-Institute-Research-Shows-Ransomware-Attacks-on-Healthcare-Delivery-Organizations-Can-Lead-to-Increased-Mortality-Rate
- Caldwell T. (2011). Ethical hackers: Putting on the white hat. Network Security, 2011(7), 10-13. https://doi.org/10.1016/S1353-4858(11)70075-7
- Cipriani M. (2016, July 29). Pokemon ‘Gone:' Players banned from Allegheny Health Network facilities. Pittsburgh's Action News 4. www.wtae.com/article/pokemon-gone-players-banned-from-allegheny-health-network-facilities-1/7481333
- Culbertson N. (2021, August 6). The skyrocketing volume of healthcare data makes privacy imperative. Forbes. www.forbes.com/sites/forbestechcouncil/2021/08/06/the-skyrocketing-volume-of-healthcare-data-makes-privacy-imperative/?sh=6ab051626555
- DeGaspari J. (2010). Staying ahead of the curve on data security. Healthcare Informatics, 27(10), 32-34, 36.
- Ekran. (2023, March 22). 7 examples of real-life data breaches caused by insider threats.www.ekransystem.com/en/blog/real-life-examples-insider-threat-caused-breaches
- Kath H. (2021, June 1). The top 10 healthcare data breaches of 2020. FORTRA. www.goanywhere.com/blog/the-top-10-healthcare-data-breaches-of-2020
- Greenberg A. (2015, April 1). Human error cited as leading contributor to breaches, study shows. SC Media. www.scmagazine.com/home/security-news/human-error-cited-as-leading-contributor-to-breaches-study-shows
- Griffith E. (2022, February 15). What is cloud computing? PC Magazine. www.pcmag.com/article2/0,2817,2372163,00.asp
- Guccione D. (2015, July 20). Is the cloud safe for healthcare? Healthcare Innovation. www.hcinnovationgroup.com/cybersecurity/privacy-security/article/13025478/is-the-cloud-safe-for-healthcare
- Gyan Solutions. (2023, February 6). How blockchain will disrupt the healthcare and life sciences sector.https://gyan.solutions/blog/blockchain-will-disrupt-the-healthcare-sector
- Health Information and Management Systems Society. (2019). 2019 HIMSS cybersecurity survey. www.himss.org/sites/hde/files/d7/u132196/2019_HIMSS_Cybersecurity_Survey_Final_Report.pdf
- Health Information and Management Systems Society. (2022). 2022 HIMSS healthcare cybersecurity survey report.www.himss.org/resources/himss-healthcare-cybersecurity-survey
- Jansen W., & Grance T. (2011, December). National Institute of Standards and Technology (NIST): Guidelines on security and privacy in public cloud computing. https://nvlpubs.nist.gov/nistpubs/Legacy/SP/nistspecialpublication800-144.pdf
- Marr B. (2020, April 20). These 25 technology trends will define the next decade. Forbes. www.forbes.com/sites/bernardmarr/2020/04/20/these-25-technology-trends-will-define-the-next-decade/#21106dd829e3
- McKeon J. (2023, February 16). Third-party data breach corrupts medical records at NH hospital. HealthITSecurity. https://healthitsecurity.com/news/third-party-data-breach-corrupts-medical-records-at-nh-hospital
- Miliard M. (2017, April 13). How does blockchain actually work for healthcare? Healthcare IT News. www.healthcareitnews.com/news/how-does-blockchain-actually-work-healthcare
- Milijkovac I. (2022, July 27). What is hacking? Types of hackers and examples. Security Gladiators. https://securitygladiators.com/threat/hacking
- Mowry M., & Oakes R. (2011, June 23). Not too tight, not too loose. Healthcare Innovation. www.hcinnovationgroup.com/home/article/13012462/not-too-tight-not-too-loose
- O'Driscoll A. (2023, March 22). The role of human error in cybersecurity: What the stats tell us. Comparitech. www.comparitech.com/blog/information-security/human-error-cybersecurity-stats
- Pennsylvania State University, Office of Information Security. (n.d.). What is phishing?http://phishing.psu.edu/what-is-phishing
- Perlroth N. (2020, October 3). Clinical trials hit by ransomware attack on health tech firm. New York Times. www.nytimes.com/2020/10/03/technology/clinical-trials-ransomware-attack-drugmakers.html
- Ponemon Institute. (2015, May 27). Fifth annual benchmark study on privacy & security of healthcare data.www.ponemon.org/research/ponemon-library/security/fifth-annual-benchmark-study-on-privacy-security-of-healthcare-data.html
- Rosencrance L. (n.d.). Definition: Social engineering. TechTarget. http://searchsecurity.techtarget.com/definition/social-engineering
- Salesforce UK. (2020, October 1). What are the advantages of cloud computing? 10 reasons to move to the cloud. Salesforce. www.salesforce.com/uk/blog/2015/11/why-move-to-the-cloud-10-benefits-of-cloud-computing.html
- Schwartz S. (2022, January 25). Careless employees behind the majority of insider threat incidents: Report. CIO Dive. www.ciodive.com/news/insider-threat-malicious-negligent-employee/617715
- Software Testing Help. (2023, July 5). Top 11 most powerful cybersecurity software tools in 2023. www.softwaretestinghelp.com/cybersecurity-software-tools
- Sullivan T. (2012, May 23). DHS lists top 5 mobile medical device security risks. Healthcare IT News. www.healthcareitnews.com/news/dhs-lists-top-5-mobile-device-security-risks
- Terwillegar T. (2023, July 17). 10 essential password security best practices. Liquid Web. www.liquidweb.com/blog/password-security-best-practices
- U.S. Department of Health and Human Services. (2006, December 28). HIPAA security guidance. www.hhs.gov/sites/default/files/ocr/privacy/hipaa/administrative/securityrule/remoteuse.pdf
- U.S. Department of Health and Human Services. (2017, June 7). HHS settles with health plan in photocopier breach case.www.hhs.gov/hipaa/for-professionals/compliance-enforcement/examples/health-plan-photocopier-breach-case/index.html
- U.S. Food and Drug Administration. (2022). Medical device cybersecurity: What you need to know.www.fda.gov/consumers/consumer-updates/medical-device-cybersecurity-what-you-need-know
- Waddell K. (2016, February 17). A hospital paralyzed by hackers. The Atlantic. www.theatlantic.com/technology/archive/2016/02/hackers-are-holding-a-hospita1s-patient-data-ransom/463008


